Back
Top 10 Agentic Pen Testing Software Solutions

‘What’s the worst that could happen?’ is a question you might encounter in cybersecurity. There are multiple good reasons to do penetration testing. Beyond identifying and verifying vulnerabilities, assessing controls, prioritizing risks, and meeting compliance, pen testing challenges your assumptions. It reveals whether you truly covered all angles when setting up defenses. Blind spots can creep into any architecture, so having someone with a fresh perspective assess your setup from an adversary’s point of view, can uncover weaknesses you might have missed.
70% of organizations find AI highly effective in detecting previously undetectable threats. Unlike your run-of-the-mill LLM, Agentic AI, when applied to pen testing, can autonomously or semi-autonomously conduct pen tests by simulating real-world cyberattacks on a system. If you have heard about this new method and are keen to try it, the next step is deciding between the smorgasbord of pen-testing software solutions.
What are Agentic Pen Testing Software Solutions?
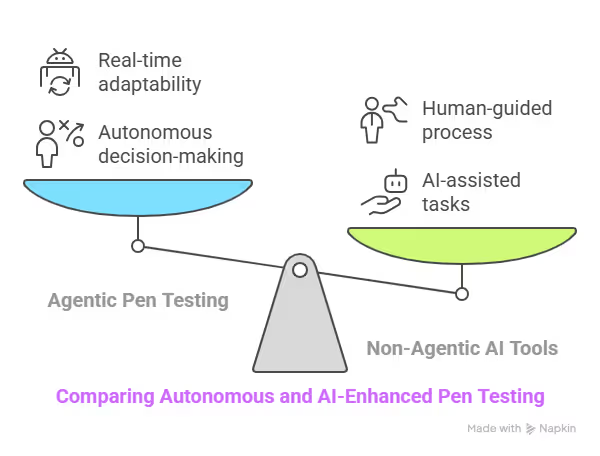
Agentic pen testing software solutions are autonomous decision-making tools that simulate real-world attackers. They exploit systems, identify vulnerabilities, and adapt their approach in real-time without needing constant human input.
Any AI-powered algorithm or model that is self-sufficient enough to form opinions and act upon them is called an AI agent. In addition to learning and considering human input, it can typically sense other AI agents and the environment in which it operates. An agent is similar to a microservice but is positioned within the control flow and can make decisions on the go.
Not all the software tools presented in this article use AI Agents. Agentic pen testing is a new technology, so you are far more likely to find tools that simply leverage AI technologies. Some tools may also use standard ML automation, which relies on trained models and predefined rules and workflows to execute attacks continuously, with little adaptability to adjust tactics.
While AI-based and Agentic AI tools use AI and automation to make a pen tester’s job easier, AI Agents can make judgments and decisions that significantly speed up and improve the pen testing process.
While the name ‘penetration testing’ is monolithic, it can be broken down into two broad classes of tests. The more common pen testing is done on networks, infrastructure, and architecture. These system vulnerabilities have been persistent and known for a while, so automated pentesting solutions are not new (Pentera, Horizon3). However, with web apps, the complexity of potential attacks is larger, and each potential exploit requires multiple steps or vulnerabilities that can’t be easily hardcoded. This has made automation more challenging to achieve and is one of the reasons agentic AI is such a game-changer.
Remember that no matter your chosen tool, you need a scoping meeting with the tool’s operators to define your app’s weaknesses, security, and business goals.
Benefits of Agentic Pen Testing Software Solutions
Before we dive into the specific benefits of Agentic AI for pen testing, the value of Agentic AI, albeit a new solution, is already evident in cybersecurity. A study by AIMultiple found that implementing an agentic AI platform can result in:
- A 52% reduction in incident response times through automation and integrated playbooks.
- A 47% increase in visibility across Microsoft 365, Cisco, and Palo Alto stacks.
- A 275% expansion in MITRE ATT&CK coverage enables better resource prioritization.
In the case of pen testing, the impact can be even more dramatic, and the benefits are endless.
1. Reduced Manual Effort, Time, and Resources Needed
Almost everything ends up revolving around money. An Agentic AI pen testing tool can reduce the workload of the pentesters while still allowing them to complete more scenarios with less time and resources. Since many pen testing contracts are payable by time spent, you can get more value for your investment by choosing an Agentic AI tool.
2. Real-World Attack Insights with Faster Detection
In the ‘old’ days, pen testers had to track new threats and write custom payloads for each unique app. Since finding two web apps configured and written the same is rare, each attack path differed. With Agentic AI, much of that work can now be relegated to the Agents, and a fully detailed, human-written script is no longer needed to complete the simulated attack. The agents can perform complex hacks and offer a detailed report of each step.
3. Scalability for Large-Scale Assessments
Enterprise companies have hundreds and sometimes thousands of constantly changing apps, and each can be exceedingly complex in its construction and the options it allows a user to choose from. An Agentic AI pen testing tool can easily help scale coverage across the entire attack surface of applications while still guided by human intelligence.
Key Features to Look For in Agentic Pen Testing Software Solutions
1. Business context-aware Attack Simulations
Since each web app is unique, so should each pen test that targets it. It’s vastly different to gain access to an app aiming to obtain admin access so you can lock up the app and demand ransom, gain access to it to steal user private information or transfer money to an undisclosed third party. Context is everything. Even if each of these attacks ended up using the same vulnerabilities (very unlikely), knowing the context of the business and the potential harm is key in designing and executing it.
2. Continuous Pen Testing
It’s not enough to prove your app is relatively safe at a single point in time. Adversaries don’t wait, and your app is constantly being updated, potentially introducing new vulnerabilities. Penetration testing should be continuous, just like QA and integration tests. One of the most effective ways to do this is by linking pen testing to your repository’s pull requests so that each app update triggers a new test. This way, whatever changes are made, you can catch any new exploits that may have slipped in along the way.
3. Real-Time Reporting and Dashboards
The cyber-world moves very fast. A new CVE can be discovered in the morning; by noon, real-world examples of exploitation could already exist. It’s critical that the defenders can move at least as fast as the attackers. Whatever tool you choose should include real-time reporting for dynamic security risk assessments so you can see immediately what went wrong, where, and how best to mitigate it.
4. Advanced Exploitation Capabilities
Adversaries already leverage dark LLMs and automation that allow them to exploit faster and more creatively than ever. Some of the most complex web app attacks will likely include multiple vulnerabilities and steps. If the tool you choose can only test for low-hanging fruit (easy to find and patch, single library vulnerabilities), it’s not the tool you’re looking for. Look for a tool to chain multiple weaknesses and utilize scripting to complete the hack.
5. Actionable Prioritization and Remediation Guidance
So, the pen testing tool managed to exploit a vulnerability and even explained how. But if the fix is just “update the library to the latest version” or “block super user access,” that might not be enough. Sometimes, your developers depend on a particular library’s version, or the super user needs to take a specific action. A good tool would be able to offer a more nuanced and context-aware remediation that takes the company’s needs into account.
Additionally, there could be far more vulnerabilities than could be addressed in a reasonable time frame. That’s why it’s essential to get actionable prioritization based on business context, exact proof of exploitability provided (is it a challenging exploit or one that a school grader could do), potential business harm (a dollar figure is a good scale), for example, and not just a vulnerability’s CVSS score. With exact prioritization, it’s easier to decide where and how to assign resources to start fixing bugs.
6. Human Involvement
There is no substitute for good old human ingenuity. Therefore, a good agentic pen testing software tool will include a human-in-the-loop mechanism that evaluates AI agents and their findings. When it comes to those deep, complex use cases, humans still need to guide and approve the actions taken by the agents, with the additional option of offering complex manual tasks that complement the agent’s work.
Top 10 Agentic Pen Testing Software Solutions
1. Metasploit
Metasploit is a Ruby-based open-source framework created in collaboration between the open-source community and Rapid7 in 2003. The platform provides out-of-the-box exploits, payloads, auxiliary functions, encoders, listeners, shellcode, post-exploitation code, and nops (instructions to keep a payload from crashing).
The software has an extensive knowledge base and numerous tutorials online, including a dedicated YouTube channel. Metasploit is built for hands-on usage, so it’s not for you if you’re uncomfortable in a command–line environment or have no coding experience.
Best for SMBs’ infrastructure scanning and exploitation.
“Metasploit is the best tool for creating payloads and exploiting systems, and it is the best tool for hackers. We can create different types of payloads with this framework, like apk, exe, and PDF.”
2. Terra Security
Terra Security goes beyond AI pen testing to offer the first-ever agentic AI platform for offensive security, focused on web application pen testing and red-teaming. Controlled by a human-in-the-loop mechanism, Terra's AI agents perform thousands of best-of-breed tests for an entire attack surface coverage with compliance mechanisms from start to finish.
Terra’s agentic-AI platform is run by the Terra team as a service, so you don’t need to worry about how to use it. You just need to let the company know what you're most worried about in your web app; they do the rest. In white-boxing, Terra offers context-aware continuous testing of your app based on PR changes. It also provides a reporting and prioritization layer based on unique business risks.
Best for: Deep Web app pen testing and continuous pen testing.
“With agile releases, even small updates can introduce new threats. Terra's continuous Agentic change-based pentesting is transformative, ensuring every new or updated feature gets promptly evaluated for exploitable vulnerabilities.”
3. Horizon3.ai
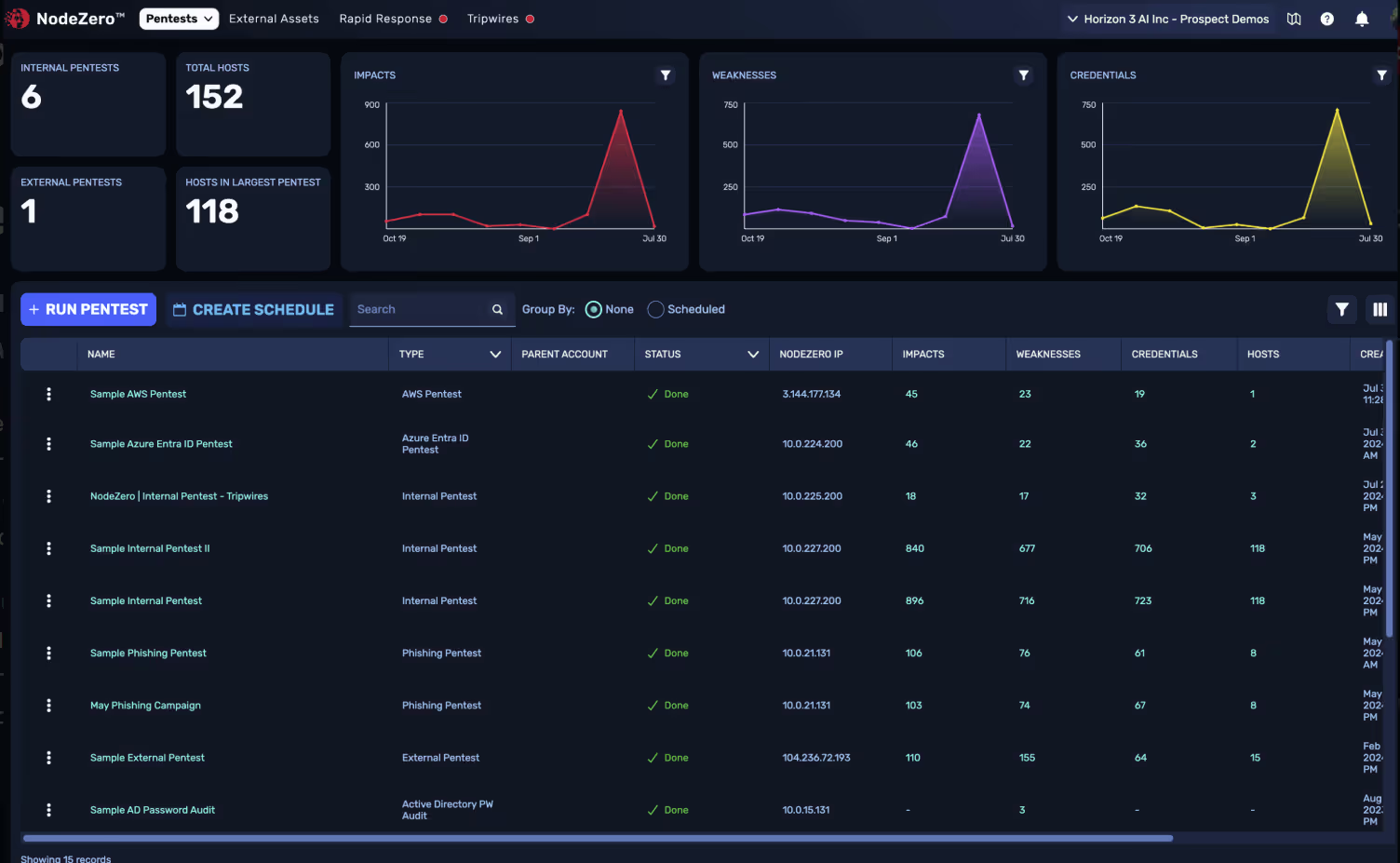
NodeZero™ is an autonomous security platform offered as a self-service SaaS from Horizon3.ai. It continuously identifies, ranks, addresses, and confirms the remediation of exploitable attack surfaces and vulnerabilities. Security posture blind spots, including readily compromised credentials, unprotected data, and misconfigurations, are all highlighted and organized in order of severity. The platform utilizes AI algorithms, including knowledge graph analytics and inference engines, to autonomously navigate and attack a network like a real-world attacker.
Best for: Network/infrastructure pen testing, enabling organizations to perform cloud-focused pen tests across their AWS and Azure environments.
“Finding the misconfigurations that have been inherent to an environment for years. Finding weaknesses that I didn't realize were an issue. Finally, Rapid Response can alert you of existing new vulnerabilities that are exploitable.”
4. Cobalt Strike
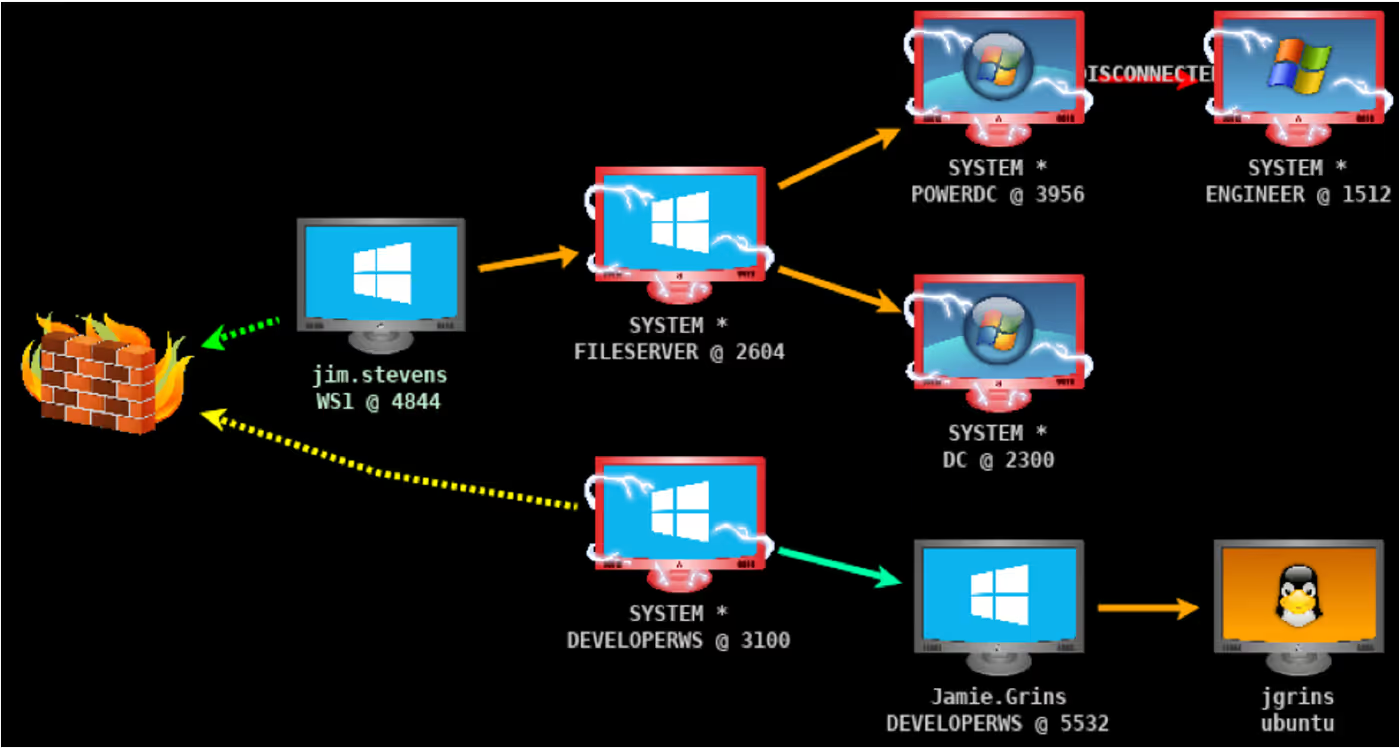
Cobalt Strike includes a command and control (C2) framework that enables attackers to manage the data and outcomes of their operations and remotely control and monitor their activities. The tool can stealthily infiltrate networks, steal sensitive information, and evade detection. It includes a team server, social engineering capabilities, and post-exploitation features. The system doesn’t boast explicitly labeled AI-driven capabilities and relies exclusively on operator skill and knowledge.
Best for: Black box network pen testing.
“The best thing about Cobalt Strike is that it provides red teamers and pentesters with built-in modules for crafting targeted attacks. The Beacon functionality of Cobalt Strike has been top-notch for ages.”
5. Pentera

Pentera provides an automated security validation platform that harnesses AI to simulate real-world attacks across an organization's whole attack surface, including networks, cloud environments, and applications. Its AI engine conducts simulations that replicate threat actor behavior, helping security teams uncover vulnerabilities before adversaries do. The platform prioritizes weaknesses, delivers actionable remediation guidance enriched with business context, and generates comprehensive reports. With an on-demand testing model, Pentera enables semi-continuous validation of security controls to keep defenses effective.
Best for: Medium to Enterprise systems and infrastructure pen testing.
“The most striking benefit is the ability to go from point in time, sample-based testing to continuous validation and testing ensures better overall security outcomes.”
6. AttackIQ
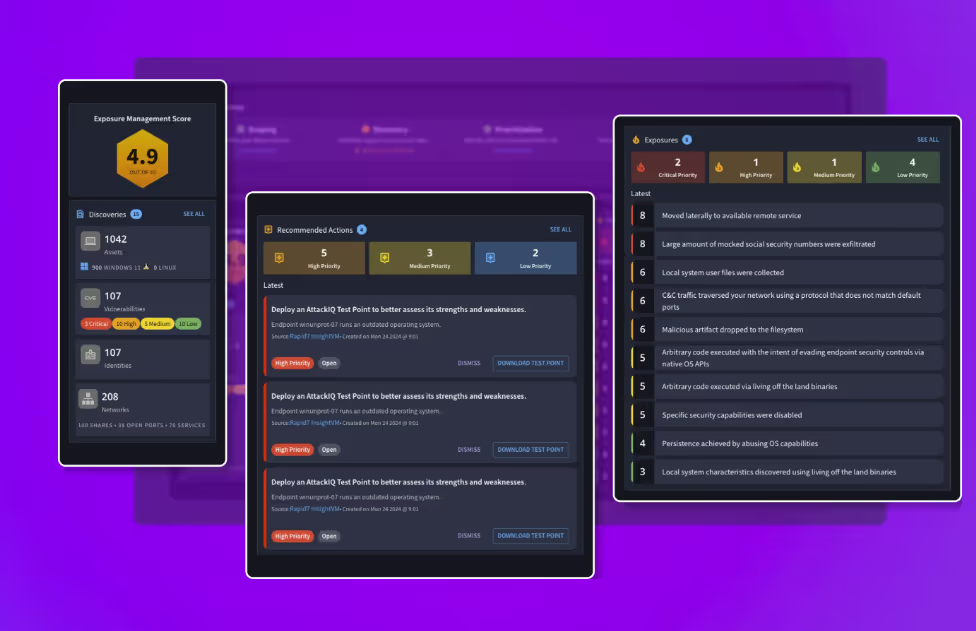
AttackIQ is a Breach and Attack Simulation (BAS) platform that helps companies test and improve their security posture. It can simulate real-world attack scenarios based on known techniques used by actual adversaries. The platform offers automated testing capabilities and pre-built test templates to make the red team’s work easier. The system uses AI to keep its attack offerings up to date, as well as AI-driven risk prioritization and attack path analysis.
Best for Medium to large businesses' infrastructure security validation.
“The best part is that it is easy to use and packed with many features.”
7. Caido
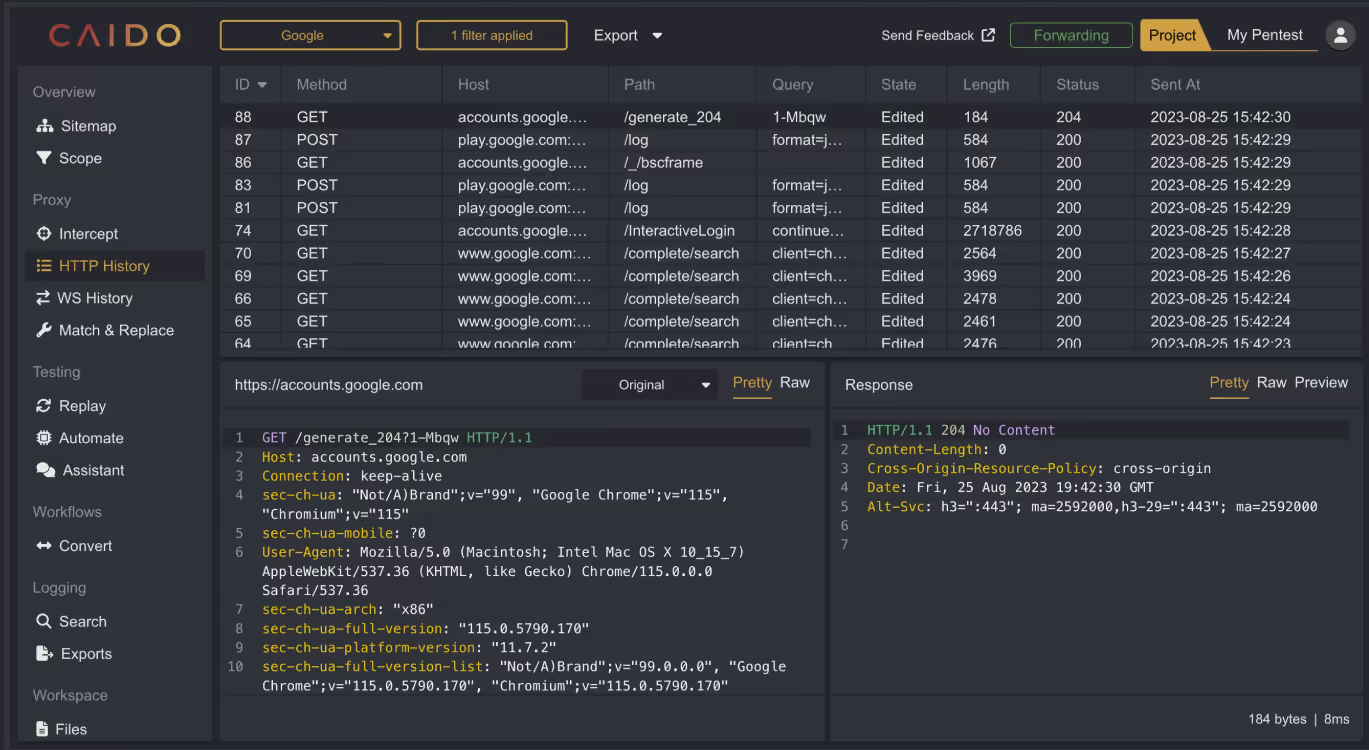
Caido is an open-source web application security testing proxy written in Rust. As a community project, the platform is highly extensible through plugins and scripting, allowing users to customize it to their needs and workflows. It offers a free and paid Pro option. Caido Pro includes an "Assistant" feature powered by an AI LLM specifically tailored for security research. As an example, the assistant can generate proof-of-concept code for Cross-Site Request Forgery (CSRF) attacks based on a provided request.
Best for: Web application scanning and penetration testing from individual testers to the enterprise level.
“Caido is a new and up-and-coming web application proxy tool. The development team regularly updates it, and it has some useful functionality for penetration testers. However, it has not reached its full potential yet.”
8. Invicti
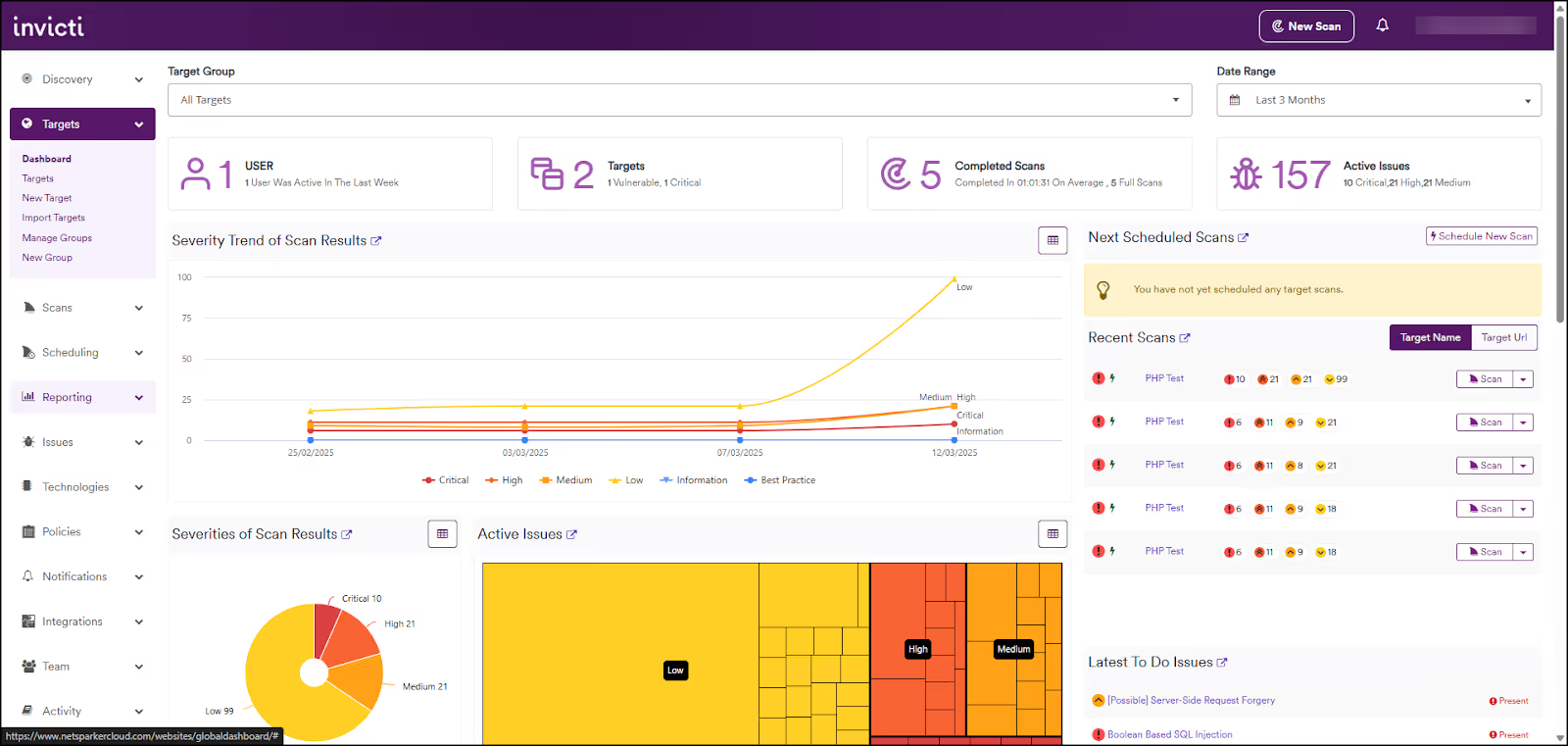
Invicti offers Dynamic Application Security Testing (DAST), Interactive Application Security Testing (IAST), and Software Composition Analysis (SCA) for web application security. It integrates well with CI/CD pipelines and leverages OpenAPI and Swagger files to test well-documented REST APIs.
Invicti’s AI-enabled Predictive Risk Scoring feature allows organizations to prioritize the most vulnerable applications and focus their testing and remediation efforts accordingly. It also offers proof-based scanning, which reduces false positives by providing evidence of vulnerability exploitation.
Best for SMBs' web application and API scanning.
“Simple API integration, Ability to schedule scans & report valuable vulnerabilities removing noise in the process.”
9. Burp Suite
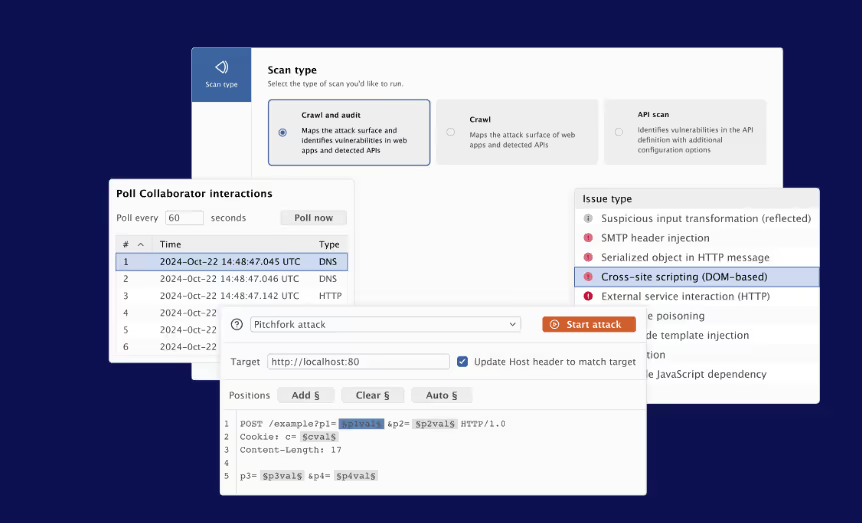
Burp Suite is a web application security and penetration testing tool with a comprehensive suite of integrated tools. It supports in-depth manual analysis, automated vulnerability discovery (in the Professional version), and an extensive library of community-developed and PortSwigger-created extensions to tailor the tool to specific testing needs. As of March 31st, 2025, Burp Suite introduced Burp AI for the users of Burp Suite Professional, providing AI-driven insights, automation, and efficiency improvements.
Best for SMBs' web application penetration testing.
Review:
“I love that it’s a wonderful penetration tool with properties like network scanning, network intrusion, vulnerability assessment, and many more.”
10. Aptori

Aptori uses autonomous testing to identify business logic flaws and security vulnerabilities early in the development lifecycle. In the development phase, it can automatically generate and execute tests (including API tests), allowing developers to focus on building features rather than writing tests. Aptori can integrate with various CI/CD pipelines and offers AI-powered code fixes to streamline remediation. As a human-in-the-loop feature isn’t inherently built-in, any wide deviation from the presented automation might present unexpected difficulties.
Best for SMBs' web application and API scanning.
The Future of Pen Testing is Agentic
Let’s start with a few inalienable truths: demand for pen testing will grow, AI use will rise for offense and defense, vulnerabilities will keep emerging, and software complexity will increase misconfiguration risks. Based on these truths, the only reasonable course of action is a tight integration of human ingenuity and creativity with the speed and power of AI for cybersecurity defense. Platforms integrating AI agents exemplify this approach.
While AI-enabled pen-testing platforms often focus on automation, those with integrated AI agents offer real-time adaptability and can handle complex cases without constant human input.
Terra combines human expertise with the scalability of AI agents, allowing for the scripting of multi-step attacks and reasoning across the testing process. Explore more here.
Be the first to experience the future of security.
Secure your spot by leaving your email








