Back
External Penetration Test: What is it & How to Perform One Reliably

As a cybersecurity practitioner, do you know where your cyber perimeter begins - and where it ends? Your perimeter now comprises every internet-facing asset your company has ever deployed, from cloud workloads to APIs, login portals, partner integrations, and CI/CD tools. Even employees' email accounts and cellphones could be potential attack vectors.
79% of cyber risks are outside a company’s internal IT perimeter. Thanks to the rise of Ransomware-as-a-Service platforms, it’s now easier than ever to target companies with ransomware and create new blind spots and open access points.
Since we’re all human and biases and blind spots are part of the deal, running an external penetration test to check out how robust your defence plan is when tested against a ‘real’ targeted attack can be beneficial. But how should you approach it?
What is an External Penetration Test?
An external penetration test simulates how a real attacker might attempt to breach a company’s internet-facing systems. Conducted from outside the organization’s network, it replicates tactics used to steal data, disrupt services, or exploit exposed infrastructure. The goal is to assess how well perimeter defenses hold up under realistic threat conditions.
Unlike internal tests, this exercise focuses strictly on assets exposed to the public internet: web applications, APIs, cloud services, login portals, and publicly accessible servers. Penetration testers use a combination of reconnaissance, automated scanning, and manual exploitation to uncover potential entry points.
Common issues uncovered include unpatched software, misconfigured services, exposed ports, and injection vulnerabilities like SQL and cross-site scripting. The test concludes with a report that lists the findings, explains their potential business impact, and provides clear, prioritized recommendations for remediation.
These tests can be conducted by in-house security teams and external consultancies or delivered through pen testing as a service (PTaaS), which is typically more scalable and flexible.

Who Needs an External Penetration Test?
Industries that handle sensitive data, are heavily regulated, or have a significant online presence benefit the most from external penetration testing because they are at higher risk of large-scale disruption. The list includes:
- Finance: banks, credit card companies, payment companies
- Healthcare: hospitals, insurance providers
- E-commerce: online retailers processing payments
- Technology: SaaS providers, software companies
- Government entities
While continuous penetration testing helps maintain security over time, it’s particularly critical to run targeted external tests after major infrastructure changes, such as launching new apps, opening APIs, or migrating to the cloud.
They are also crucial after deploying machine learning or AI systems that influence core operations, especially if those models interface with public APIs or control sensitive logic. Operational triggers like model drift or adjustments can unintentionally expose new vulnerabilities by altering decision boundaries, access flows, or data exposure patterns, making these systems prime candidates for targeted testing.
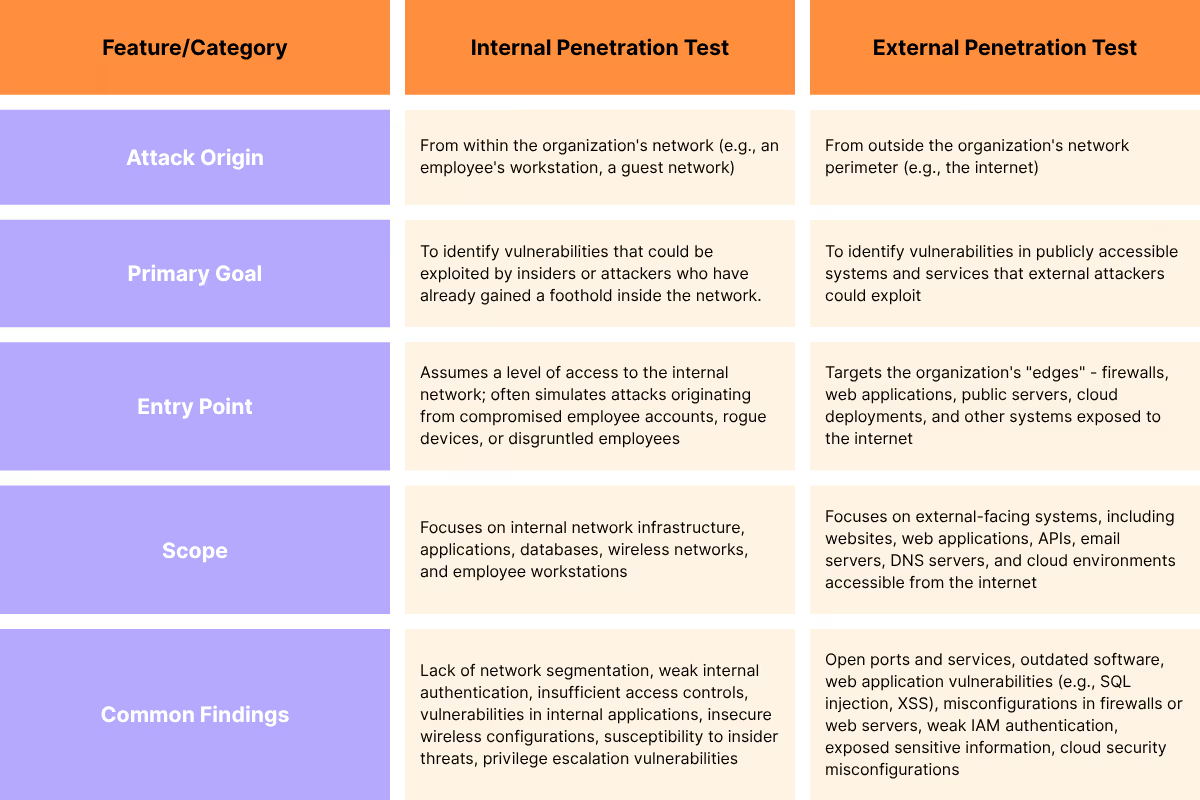
Internal vs External Penetration Test: Key Differences
How to Perform an External Penetration Test Reliably
1. Correlate Asset Discovery with Business Context
Penetration testing becomes far more valuable when aligned with business priorities. Work with stakeholders to build a risk profile that reflects the organization’s unique structure, critical assets, and regulatory obligations.
Then, correlate asset discovery with real-world risk and organizational context. This alignment will help you focus on systems with the highest operational, financial, or reputational impact and reinforce your cyber resilience strategy.
Tools like Censys and Shodan can then identify publicly exposed infrastructure. Pen testers and internal teams should also regularly scan domains and IP ranges to detect shadow IT, misconfigured services, and forgotten assets that may be unintentionally exposed.
The key is to prioritize testing based on impact, not just exploitability. For example, a simple flaw on a low-value blog server poses minimal risk, while the same issue on a customer-facing API could lead to serious consequences.
2. Use Passive Recon First to Avoid Premature Detection
Passive reconnaissance is a low-risk, high-yield method to surface exposed digital assets before an external penetration test. By analyzing DNS records, WHOIS data, and subdomain history, you can identify discrepancies between your formal asset inventory and what's accessible online.
This step helps uncover unmanaged infrastructure, legacy services, or shadow IT that you may not be tracking internally, but still expand your external attack surface.
Mandate passive recon as a precondition for external testing, and review these findings so you know where the pen testing team should focus their efforts. The testing scope should prioritize customer-facing applications, revenue-driving APIs, or systems tied to regulated or sensitive data.
After this initial mapping, teams can move on to active scanning and exploitation, using manual methodologies and web application penetration testing tools to probe for misconfigurations, injection flaws, or authentication issues.
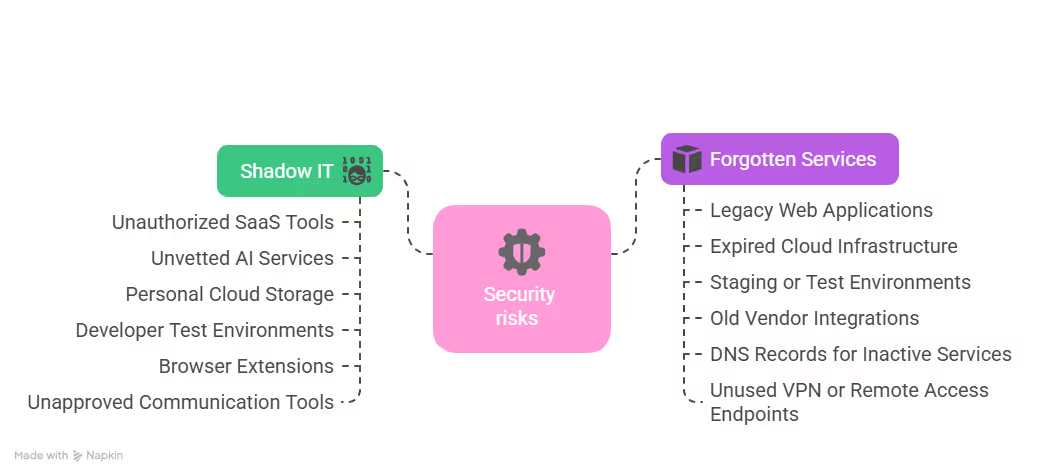
3. Identify and Investigate Shadow IT and Forgotten Services
Shadow IT (tech used without formal IT approval) or forgotten services that were never properly decommissioned are a serious gap because they both fall outside the scope of regular monitoring and patching. Consider, for example, unauthorized AI tools, open-source software installed during development, or test environments left running in production.
The 2023 Microsoft AI data exposure is a textbook case study: Researchers inadvertently leaked 38TB of internal data by embedding a misconfigured Shared Access Signature (SAS) token in a public GitHub repository. The token provided full access to an Azure Blob Storage container tied to a forgotten AI research environment that had long fallen outside Microsoft’s formal monitoring and governance processes.
Continuously identify, monitor, and retire any unused or unsanctioned services, regardless of their perceived importance. Open-source tools like OWASP Amass provide active scanning capabilities that can reveal unknown or outdated internet-facing assets.
4. Continuously Map the External Attack Surface
No company is static, regardless of its size. They constantly evolve and change, which is true of their technology and potential attack surfaces. That’s why you and your external testers must continually map and update your network access points, especially old or underused ones.
The more complex the system and the more legacy services exist, the more chances there are of hidden access points your company forgot about, never knew about, or didn’t bother to patch or update because they were low priority. Any scanning tools already mentioned could aid in finding such tempting attack targets.
It’s important to redo the scan periodically and pair it with web app security best practices. Build in secure defaults from the start rather than relying solely on detection and remediation after the fact.
5. Incorporate Expert Human Pen Testers
Humans bring critical thinking, creativity, and contextual understanding that automated tools, including AI, lack. They can identify novel attack vectors, chain seemingly innocuous vulnerabilities, and adapt their approach based on real-time observations and the specific nuances of the target environment.
This is because they often better understand the underlying business logic of the tested environment and can assess the real-world impact of vulnerabilities more intuitively than other tools. The best combination, of course, is a human in the loop rather than a human doing everything. Having a human make the creative decisions while an AI does the grunt work would offer the best of both worlds - the creativity and intuition of a human with the power and speed of AI.
6. Chain Vulnerabilities Across Hosts
Most scanning tools return a list of CVEs after a vulnerability scan, but real-world attacks rarely hinge on just one. Instead, attackers often chain multiple vulnerabilities across systems, users, and environments. They follow the path of least resistance until they reach their target: privileged access, sensitive data, or control over critical infrastructure.
A clear example is the Kaseya VSA attack in July 2021. Attackers exploited zero-day flaws in Kaseya’s remote management software to breach multiple MSPs and then used their access to deploy ransomware across hundreds of downstream customer environments. External pen tests should account not just for your systems but also the services and providers you rely on, as their compromise can become your compromise.

Penetration testing solutions like Terra Security use a combination of AI agents and human expertise to simulate how an attacker would move through your environment, chaining together misconfigurations, exposed services, and low-level flaws. Remediation is far more focused, helping security teams prioritize the vulnerabilities that lead to compromise, not just those that appear on a scan.
7. Actionable and Contextualized reporting
Just as important as the test itself is getting a clear and actionable report aligned with the business context and risk that each vulnerability represents. Getting a long list of CVE vulnerabilities with their CVSS scores and recommended patches does not make for a compelling read or an easy-to-comprehend business threat assessment.
A good report should be narrative-driven and based on a clear pen testing template. Each vulnerability should include the business context (why the organization should care), the potential risk (monetary or reputational), and the suggested remediation.
Ultimately, remediation decisions rest with the organization. They should be weighed against business priorities, factoring in risk tolerance, remediation complexity, cost, and time.
Testing Organizations’ Ever-Expanding Frontier
As companies evolve, deploy new services, accelerate cloud adoption, and forget old infrastructure, their internet exposure grows. The network's edge is fluid, ever-expanding, and increasingly challenging to monitor.
Whether conducting an external pen test in-house, using a tool, or partnering with a vendor, it’s essential to recognize internal blind spots. Familiarity bias, outdated inventories, and assumptions about what’s “secure” can leave critical exposures unchecked. Regular external testing is foundational for organizations handling sensitive data and subject to stringent regulations.
Terra Security combines expert human testers with AI agents to simulate realistic attack paths and identify high-impact vulnerabilities across your external perimeter. It adapts continuously and scales as needed, delivering prioritized guidance and compliance-ready reports that focus on what matters to your business. Learn more here.
Be the first to experience the future of security.
Secure your spot by leaving your email








