Back
What is Adversarial Exposure Validation (AEV)?
_.avif)
Every app or environment has its secrets, strange edge cases, and idiosyncratic behaviour. You might think you’ve accounted for every gap, but attackers aren’t looking for the obvious. Modern attackers search for the gaps that only exist in your environment and that no one thought to test for.
In 2023, 21% of error-related breaches were caused by misconfigurations. The majority came from developers and system administrators, people trusted to build and secure the system itself. Meanwhile, most security programs keep repeating the same detection routines, even as attackers iterate and improvise.
Today’s attackers probe for overlooked vulnerabilities and move fast when they find them. Your security team needs to match that energy. Adversarial Exposure Validation can help you move from static assessments to active adversarial thinking, as a fundamentally smarter way to pressure-test your defenses.
What is Adversarial Exposure Validation (AEV)?
Adversarial Exposure Validation (AEV) is a modern approach in offensive cybersecurity that continuously tests an organization’s live environment using realistic attack scenarios. Unlike traditional, periodic, and manual penetration testing, AEV operates at scale and in real time. Its goal isn’t just to surface potential vulnerabilities but to prove whether they are exploitable under current conditions.
AEV simulates real-world threat actors' tactics, techniques, and procedures (TTPs), targeting the organization’s specific architecture, business logic, and defenses. By executing actual attack paths and observing system responses, AEV provides concrete evidence of exposure, validating the existence of a weakness and how far an attacker could get with it.
AEV adapts as the system changes because it integrates with live environments and evolving infrastructure. Therefore, it eliminates the blind spots left by point-in-time assessments and minimizes noise by filtering out theoretical risks that aren’t practically exploitable. The result is a scalable, continuous view of actual risk.
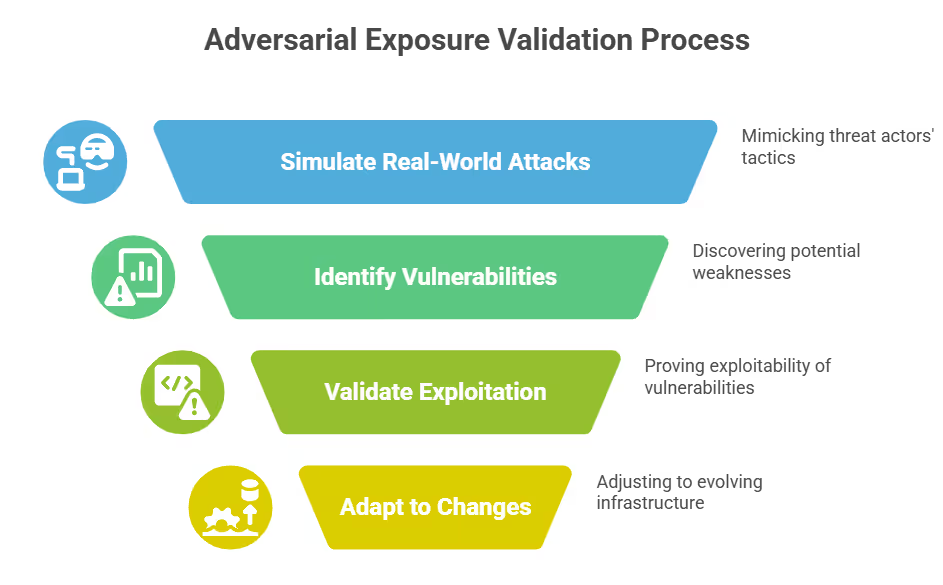
How Adversarial Exposure Validation Works: Methods vs. Processes
It’s essential to separate methods from processes to understand how AEV works. The methods refer to how AEV simulates threats, using specific technical approaches to model real attacker behavior. The processes describe the system's step-by-step workflow to map your environment, analyze risks, and validate real exposure.
Methods: Simulating Attacker Behavior
- Agentic Penetration Testing: AEV platforms leverage agentic, AI-powered testers that mimic the adaptive reasoning of skilled human attackers. These agents exploit vulnerabilities, chain attack paths, and adjust dynamically to each application's unique logic. The goal goes beyond detection to deliver proof, demonstrating how an attacker could move through your application or environment in practice.
- Breach and Attack Simulation (BAS): BAS takes a different approach by executing known attack techniques within your live environment to test how existing security controls respond. These simulations are typically mapped to frameworks like MITRE ATT&CK and help answer critical questions: Can your detection tools identify the activity? Can your defenses stop it in time?
Processes: How AEV Systems Operate
- Asset Discovery: Both methods rely on accurate asset discovery. This process involves continuously identifying all exposed and internal assets across cloud, on-premises, and hybrid environments. Without complete visibility, any simulation would leave critical areas untested.
- Threat Modeling: AEV uses threat modeling to analyze how assets interact and which components present the highest risk. This modeling is especially critical in Agentic AI-powered pen testing, where agents use that context to simulate meaningful attack paths. BAS typically works with predefined techniques and doesn’t dynamically model relationships between assets.
- Attack Path Validation: Attack path validation is unique to AI-powered penetration testing. It confirms whether an attacker could chain multiple vulnerabilities or misconfigurations to compromise a critical system. It turns theoretical findings into concrete, evidence-based risk.
- Control Validation: While not always labeled as a formal process, control validation is central to BAS. It focuses on how your defenses respond to known threats like malware or lateral movement, measuring whether they detect, block, or miss specific attack techniques. This type of validation makes BAS valuable for fine-tuning defensive posture, even though it may not uncover new exposures. AEV operationalizes threat intelligence by continuously simulating realistic adversarial campaigns to validate exposure across the attack surface.
Benefits of Adversarial Exposure Validation
- Identify Business Logic Flaws: AEV excels at uncovering vulnerabilities inside an app’s specific business processes and rules, which traditional security tools might miss. It provides a better understanding of actual exposure versus theoretical vulnerabilities.
- Simulate Real Attacker Paths: AEV replicates the complex, multi-stage TTPs real adversaries use, showing how minor vulnerabilities can be chained into impactful exploits. This approach strengthens resilience against evolving threats and delivers clear, evidence-based insight to validate security posture for stakeholders and regulators.
- Enable Continuous Penetration Testing: AEV integrates automated security assessments into your pipelines for ongoing, real-time validation of security posture. Delivered via a PTaaS model, it combines the speed and scale of automation with skilled testing, enabling faster identification and remediation of critical vulnerabilities. This adaptive feedback loop aligns with DevSecOps practices and forms the foundation for modern AEV implementations.
- Prioritize True Risk: By validating whether a vulnerability is genuinely exploitable in the organization's unique environment, AEV helps to filter out false positives and theoretical risks.
- Scale Offensive Security: AEV automates many aspects of offensive security testing, such as reconnaissance and attack execution, allowing organizations to conduct comprehensive assessments across a wider attack surface continuously. This automation translates to lower costs over time than repeated, resource-intensive manual pen testing.
5 Best Practices for Implementing Adversarial Exposure Validation
1. Check How Your Vendor Handles Business Logic Testing
Many AEV platforms struggle to identify vulnerabilities tied to business logic. These vulnerabilities often live in edge cases, workflows, or custom rules specific to your product. Confirm whether the vendor’s solution can account for these behaviours, rather than relying solely on known exploits or generic test cases.
Ask exactly where and how your input comes into play. Does the platform ingest your workflows, user roles, pricing models, or custom logic paths as part of the attack simulation rather than a one-size-fits-all approach? Is this information incorporated manually during scoping or dynamically during testing?
For example, in November 2024, a hacker discovered that Stripe could allow unlimited fee-free transactions. Discovering such a specific edge case is imperative for businesses employing the Stripe financial infrastructure platform.
2. Ask for Real Examples of Attack Path Validation
Request detailed examples of how the AEV solution identifies and validates multi-stage attack paths, ideally within environments that resemble your own. Look for evidence of how the system chains misconfigurations, privilege escalations, and lateral movement to reach critical assets. This data helps verify whether the platform can simulate realistic adversary behavior and generate meaningful output for technical and executive stakeholders.
Your security team should also be able to interpret and act on the results. Can your security engineers understand how the attack unfolded, replicate it if needed, and implement a fix? During the product demonstration, ask the vendor to walk through a real attack path uncovered by the platform and explain how they communicated it to the customer.
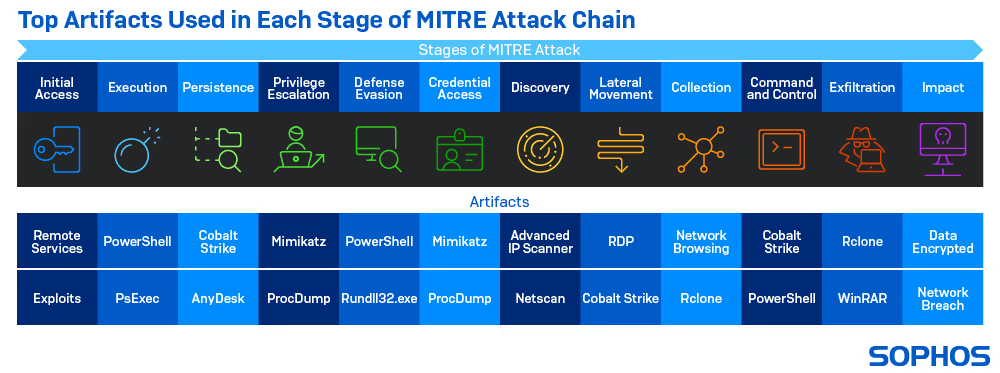
3. Check How Often TTPs Are Updated
Inquire about the frequency and methodology for updating the AEV platform's TTPs. Regularly updated TTPs ensure the AEV solution can simulate the latest attacker behaviors, leading to greater resilience against evolving attacker tactics. The most widely recognized and comprehensive central repository for adversary TTPs is MITRE ATT&CK.
Verify that your AEV vendor updates their TTPs at least as often as MITRE using the MITRE API. If updates are infrequent or manual, there's a risk your testing won't reflect the latest techniques seen in real-world intrusions.
4. Ensure Integration with Internal Security Workflows
Verify that the AEV solution integrates with your existing security tools, such as SIEM, SOAR, and ticketing systems. This integration is vital for aligning with your organisation's continuous delivery practices. Different organizations use different security tools at different points in the development lifecycle. Adding another tool to an existing cluster is much simpler than creating an entirely new testing point.
Ensure the platform supports webhook triggers, structured output formats (like JSON or JIRA templates), and permission-aware routing so critical findings reach the right team at the right time, with enough context to act.
In more complex environments, especially those combining cloud services with on-prem infrastructure, the platform should also integrate with existing practices for data centre management. Without that connection, physical systems or legacy infrastructure exposures can be missed entirely.
5. Validate Regulatory and Compliance Alignment
Ask how the AEV platform supports your specific compliance requirements, whether SOC 2, ISO 27001, PCI DSS, HIPAA, or internal policy frameworks. The platform should generate audit-ready evidence that ties validated attack paths to control objectives, with clear documentation of what was tested, what was exploitable, and how it was remediated. Generic vulnerability reports won’t cut it; your vendor should follow a penetration test report template that maps directly to compliance controls and can be exported into your GRC workflows.
Also check how the platform handles data security, credential access, and scope boundaries, especially if you’re subject to regional restrictions like GDPR or industry-specific obligations. AEV tools simulate real-world attacks, so they must prove that their processes won’t introduce compliance risks of their own. Baseline expectations include strong audit trails, scoped testing windows, and time-bound credentials. If the vendor can’t show that, it’s not enterprise-ready.
View Your Network and Apps as an Adversary Would
AEV marks a fundamental evolution in security testing, from detecting vulnerabilities in isolation to proving how they can be exploited in real-world conditions. It provides a more accurate and actionable view of risk, showing how attackers could move through your systems and how that threatens critical operations, revenue, or reputation.
Terra Security brings this approach to life with its agentic AI platform. Unlike legacy tools, Terra adapts to your business logic, integrates directly into CI/CD workflows, and delivers continuous, high-fidelity attack simulations on every code change or attack surface change. It combines the adaptability and depth of human testing with the coverage and speed of automation.
With a built-in human-in-the-loop system and context-aware reporting, every output is designed to prioritize what matters, cut through false positives, and give teams the clarity they need to act. Book a demo to learn more.
Be the first to experience the future of security.
Secure your spot by leaving your email








