Back
DAST vs Penetration Testing: Which is right for you?
%20DAST%20vs%20Penetration%20Testing_%20Which%20is%20Right%20for%20You_.avif)
Breaches keep proving a hard truth: automated tools alone aren’t enough. Attackers exploit logic gaps, chain vulnerabilities, and move faster than most teams can react. Security needs more than scans; it needs real insight into how applications can break.
In late 2024, attackers took an average of five days to exploit a disclosed flaw. By Q1 2025, over a quarter of new CVEs were targeted within 24 hours-far faster than most teams can patch, test, or respond to.
Automated DAST tools are fast, some are easy to use, and often more cost-effective than manual web application penetration testing, making them an appealing option. Pen testing goes deeper but is usually slow, expensive, and quickly outdated as your app evolves. So, how can security teams catch and fix critical flaws without blowing the budget or slowing the release cycle?
What Is DAST (Dynamic Application Security Testing)?
Dynamic Application Security Testing (DAST) is a dynamic security testing method that finds vulnerabilities in a running application. While traditionally performed in a black-box manner, testing from the outside without knowing the internal code, modern DAST tools can also operate in a gray-box mode by using information such as authentication credentials or application-specific configurations.
Like an external penetration test, DAST tools interact with the application from the outside through interfaces like web browsers, APIs, or web services to simulate real-world attacks.
They start by crawling map pages, inputs, and parameters to understand the app’s structure. Then, they launch automated attacks, sending malicious inputs and analyzing how the app responds. They detect issues like injection flaws, cross-site scripting (XSS), authentication problems, misconfigurations, and business logic errors that might only appear at runtime.
Unlike static application security testing (SAST), which inspects code without executing it, DAST focuses on runtime behavior, catching vulnerabilities related to how the application processes data, interacts with external systems, or handles user sessions. Today, DAST is often integrated into CI/CD pipelines, allowing security teams to run automated scans whenever new code is built and deployed in testing environments.
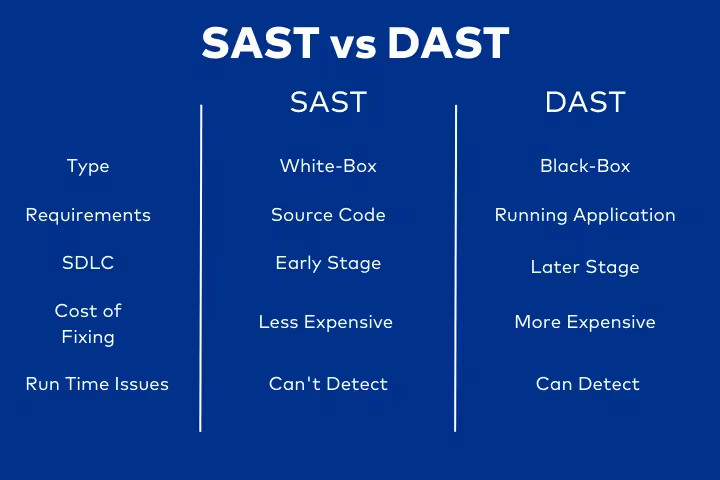
Pros of DAST
1. Language and Framework Agnostic
Because DAST interacts with the application from the outside, it often doesn't require access to the source code or understanding of the underlying programming language. It can test applications built with any technology stack, including third-party software or legacy systems where source code is unavailable.
2. Easily Integrated into CI/CD Pipelines
Modern DAST tools automate scans and integrate seamlessly into CI/CD pipelines. This allows for frequent and automated security testing with every code commit or build, increasing the chance of detecting a problem before deploying the app to production.
3. Useful for Compliance Requirements
By providing reports on identified vulnerabilities or their absence, and demonstrating ongoing security testing, DAST helps demonstrate due diligence in securing applications for audits and regulatory bodies such as PCI DSS, HIPAA, and GDPR.
Cons of DAST
1. Late in the SDLC
DAST requires a running, executable application, meaning it's typically performed later in the Software Development Lifecycle (SDLC) than SAST or SCA. Fixing critical vulnerabilities at this stage can be more costly and time-consuming, as each fix may require additional code changes.
2. Limited Code Coverage and Traceability
As a black-box testing method, DAST can only test what it can "see" and interact with through the application's interface. It may miss vulnerabilities in parts of the code that are not actively executed during the scan, and it cannot pinpoint the exact line of code where a vulnerability resides, making remediation more challenging for developers. For example, DAST often struggles to detect issues like Insecure Direct Object References (IDOR), where changing a numeric ID in a URL might expose another user’s data.
3. Challenges with Complex Workflows
DAST tools can sometimes struggle navigating complex authentication mechanisms (like multi-factor authentication) or multi-step business workflows. Getting your chosen tool to achieve full coverage in such scenarios can still require significant manual configuration.
4. Can’t Simulate Real Attacker Behavior or Assess Business Impact
While DAST simulates attacks, it lacks a skilled attacker's creativity, persistence, and human intuition. It can’t discover complex chained vulnerabilities or pivot between different systems. It also primarily focuses on technical flaws and cannot assess the business impact of a successful exploitation on organizational operations, revenue, or reputation, as it lacks awareness of business logic.
What is Penetration Testing?
Penetration testing, often called pen testing, is an authorized, simulated cyberattack on a system, network, or application. Its purpose is to find security weaknesses before real attackers can exploit them. Pen testing helps organizations assess their security risks, evaluate the effectiveness of existing defenses, and prioritize remediation efforts to protect data, meet compliance requirements, and maintain trust.
A typical pen test involves several steps, including :
- Scoping the test
- Gathering information about the target (reconnaissance)
- Scanning for potential vulnerabilities
- Attempting to exploit those weaknesses to gain access
- Documenting findings with clear recommendations for remediating them.
Pen testing can be done with automated tools, which quickly scan for known vulnerabilities and misconfigurations, or manually by skilled testers who look deeper for complex issues like business logic flaws or chained attacks.
Automated tests are fast and efficient. However, manual testing often provides a more thorough and realistic assessment of how an attacker could breach defenses, which is crucial for protecting high-value systems.
Agentic pen testing software solutions like Terra Security bridge the gap between these two methods. Their platform uses intelligent AI agents to handle large-scale, semi-autonomous testing across the entire attack surface while human experts oversee offensive actions by the AI agents, guide the agents during complex exploits and validate results.
This combination ensures both the speed and scalability of automation and the depth and precision of human expertise, delivering more accurate insights and meaningful security outcomes.
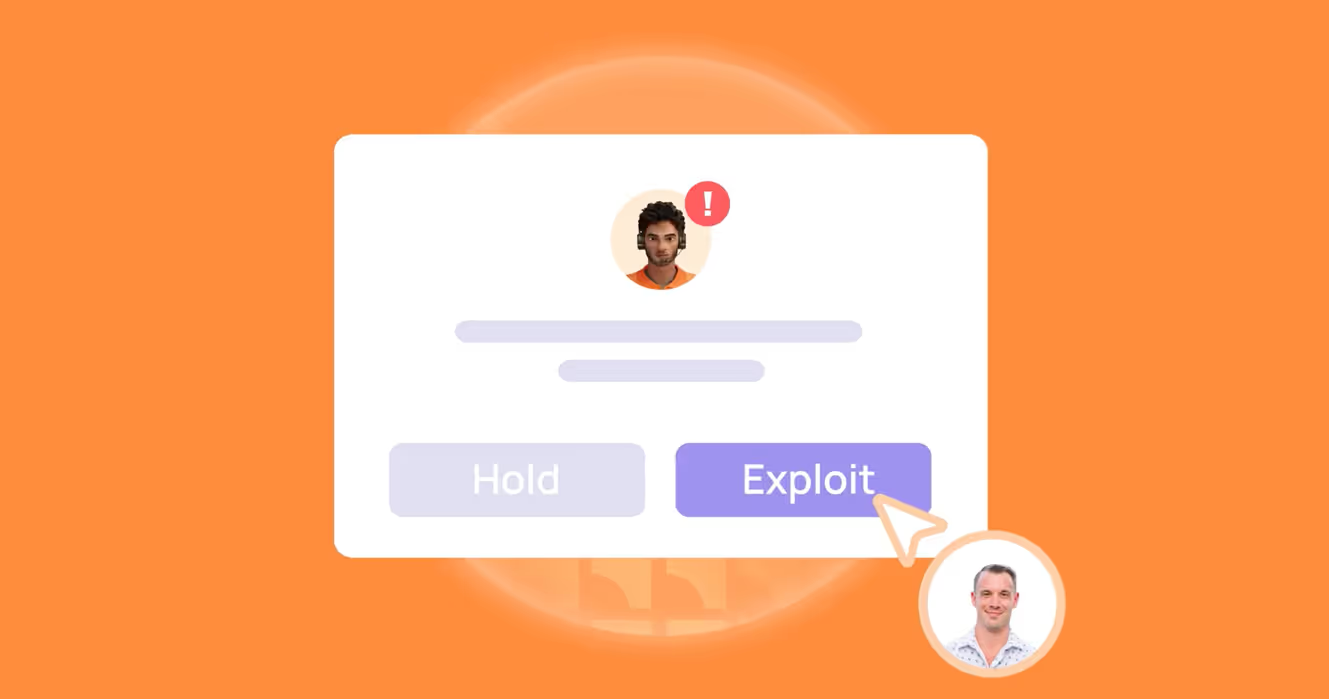
Pros of Penetration Testing
1. Simulates Real-World Attacker Behavior
Penetration tests actively and safely attempt to exploit weaknesses. They mimic real adversaries’ tactics, techniques, and procedures within a controlled, authorized scope. This hands-on approach can reveal how an attack might unfold in practice, producing concrete evidence such as unauthorized data access, privilege escalation, or lateral movement within the environment.
By demonstrating the impact of exploitation, penetration tests empower organizations to prioritize remediation efforts based on actual risk and business impact, rather than relying solely on theoretical severity scores like CVSS.
2. Uncovers Complex and Chained Vulnerabilities
Pen tests employ human creativity and intuition to chain together seemingly minor vulnerabilities to achieve a significant breach, mimicking sophisticated attack paths. This ability to think "outside the box" often uncovers flaws in business logic, configuration, or human processes that automated tools might miss. Not all pen tests consider the company’s business logic when orchestrating a breach. So, if you decide to employ a pen test, it’s preferable to choose one that does.
3. Valuable for Compliance and Risk Assessments
Many industry regulations and standards, such as PCI DSS, HIPAA, and GDPR, require regular penetration testing. Conducting these tests demonstrates due diligence in protecting sensitive data and helps organizations avoid potential fines or legal consequences.
Cons of Penetration Testing
1. Time-Consuming and Resource-Intensive
Comprehensive penetration tests, especially manual ones, demand significant time, skilled personnel, and often considerable financial investment. As a result, frequent testing is usually impractical for many organizations, which can leave security gaps between assessments.
2. Point-in-Time Nature
Penetration tests show potential exploits at a specific moment. As systems and threats constantly evolve, new vulnerabilities can emerge quickly after a test is completed, requiring ongoing security efforts. Moreover, continuous penetration testing has historically failed because automated tools alone can’t handle deep, complex attacks.
3. Inconsistent Quality Across Providers
The effectiveness and thoroughness of a manual penetration test are directly dependent on the expertise and creativity of the individual tester. A less experienced or skilled tester might miss critical vulnerabilities, creating a false sense of security.
4. Not Scalable Across Multiple Apps
Due to the highly customized nature of manual in-depth penetration testing, it's generally not feasible to perform comprehensive tests across an extensive portfolio of applications simultaneously or with high frequency. Organizations with numerous applications may find it challenging to achieve consistent, wide-ranging coverage through traditional pen testing alone.
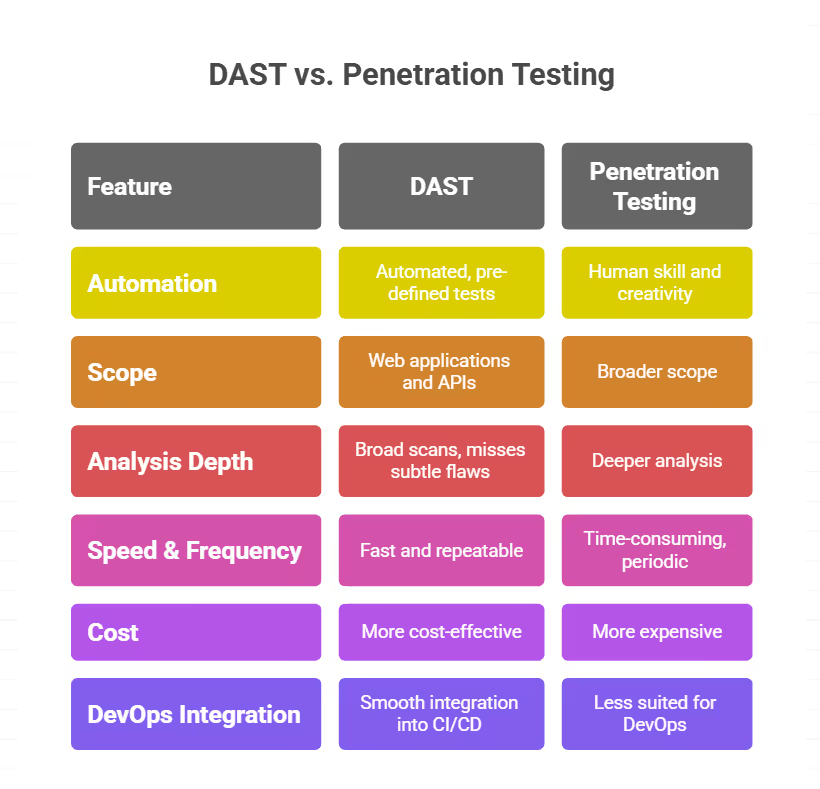
DAST vs Penetration Testing: Key Differences
1. Automation vs. Human Ingenuity
DAST runs automated, pre-defined tests that are fast and repeatable, making it great for routine scans. Penetration testing depends on human skill and creativity, with testers thinking like real attackers and adjusting their tactics to find hidden weaknesses.
2. Scope
DAST mainly scans web applications and APIs. Pen testing has a broader scope. It can encompass web applications, networks, infrastructure, cloud environments, mobile applications, and even human elements (social engineering). The scope is typically defined by the engagement, allowing for targeted assessments.
3. Depth of Analysis
DAST performs broad scans but can miss subtle flaws hidden in business logic or unique application behavior. Penetration testing dives deeper, using human expertise to uncover complex vulnerabilities and chained attack paths that automated tools might overlook.
4. Speed and Frequency
DAST is designed for speed and repeatability. It can be run continuously, often with every code commit, build, or deployment in a CI/CD pipeline, with results often generated in minutes to hours. Pen testing is a more time-consuming process due to its manual nature and the required depth of analysis. It’s performed periodically, typically quarterly or annually.
5. Cost
DAST is generally more cost-effective for continuous scanning. The primary cost is often the licensing or subscription for the automated tool. Penetration testing is typically more expensive due to the significant human effort involved, the specialized skills of the testers, and the unique nature of each engagement.
6. DevOps Integration
DAST integrates smoothly into CI/CD pipelines by dynamically scanning running applications deployed during the build process. It helps avoid last-minute security surprises and improves developer productivity metrics by keeping release cycles on track. Pen testing is typically manual and time-consuming, making it less suited for automated DevOps workflows. It’s usually performed as a separate activity outside the rapid development cycle.
DAST vs Penetration Testing: What Should You Use, and When?
DAST is ideal for teams that release code frequently, such as e-commerce providers that have stringent SaaS security best practices to follow. It catches common vulnerabilities during each deployment, helping maintain security across fast-changing applications without slowing development.
Penetration testing is best for high-stakes situations, like launching a significant new product, protecting sensitive data, or meeting regulatory requirements. It’s the right choice when you need a tailored, in-depth assessment of how sophisticated adversaries might target your systems.
In practice, most organizations benefit from both DAST for continuous, automated checks across many apps and pen testing for deep dives into critical systems where business logic and complex attack paths matter most.
However, it’s important to note that most DAST tools have fallen short in reliably finding truly exploitable vulnerabilities. They often generate significant noise and false positives because they lack context about an application’s unique business logic, user flows, and deeper architectural nuances.
As a result, while DAST can provide broad coverage, it frequently misses sophisticated vulnerabilities that require human insight and nuanced attack planning. This is why relying solely on DAST has proven insufficient for achieving comprehensive web application security.
The Best of Both Worlds
While DAST and pen testing are crucial for identifying security weaknesses, they fall short when used in isolation, particularly in modern, rapidly evolving development environments where new threats and intricate exploits constantly emerge.
Terra Security combines the best of both worlds. It utilizes AI agents capable of emulating human processes, from alert interpretation to dynamic decision-making, within the control flow.
Unlike traditional methods, agentic AI seamlessly integrates API calls, behavioral modeling, and external vulnerability databases to achieve unprecedented, comprehensive attack surface coverage while still being incorporated into the CI/CD pipeline for continuous testing on each code commit or build.
With a built-in human-in-the-loop mechanism, Terra maintains the advantage of depth, contextualization, and customization of the manual pen test while integrating the speed and scalability of automated tools. It also generates clear, actionable reports to improve and speed up remediation and compliance. Learn more here.
Be the first to experience the future of security.
Secure your spot by leaving your email








