Back
How Terra’s AI Agents Uncovered a Critical SQL Injection Missed by Traditional Tools and Manual Testers
Abstract
When security leaders first see Terra in action, one of the most common questions we hear is: “Can Terra actually find things that scanners miss?” This post answers that - with a real exploit, uncovered during a continuous penetration test.
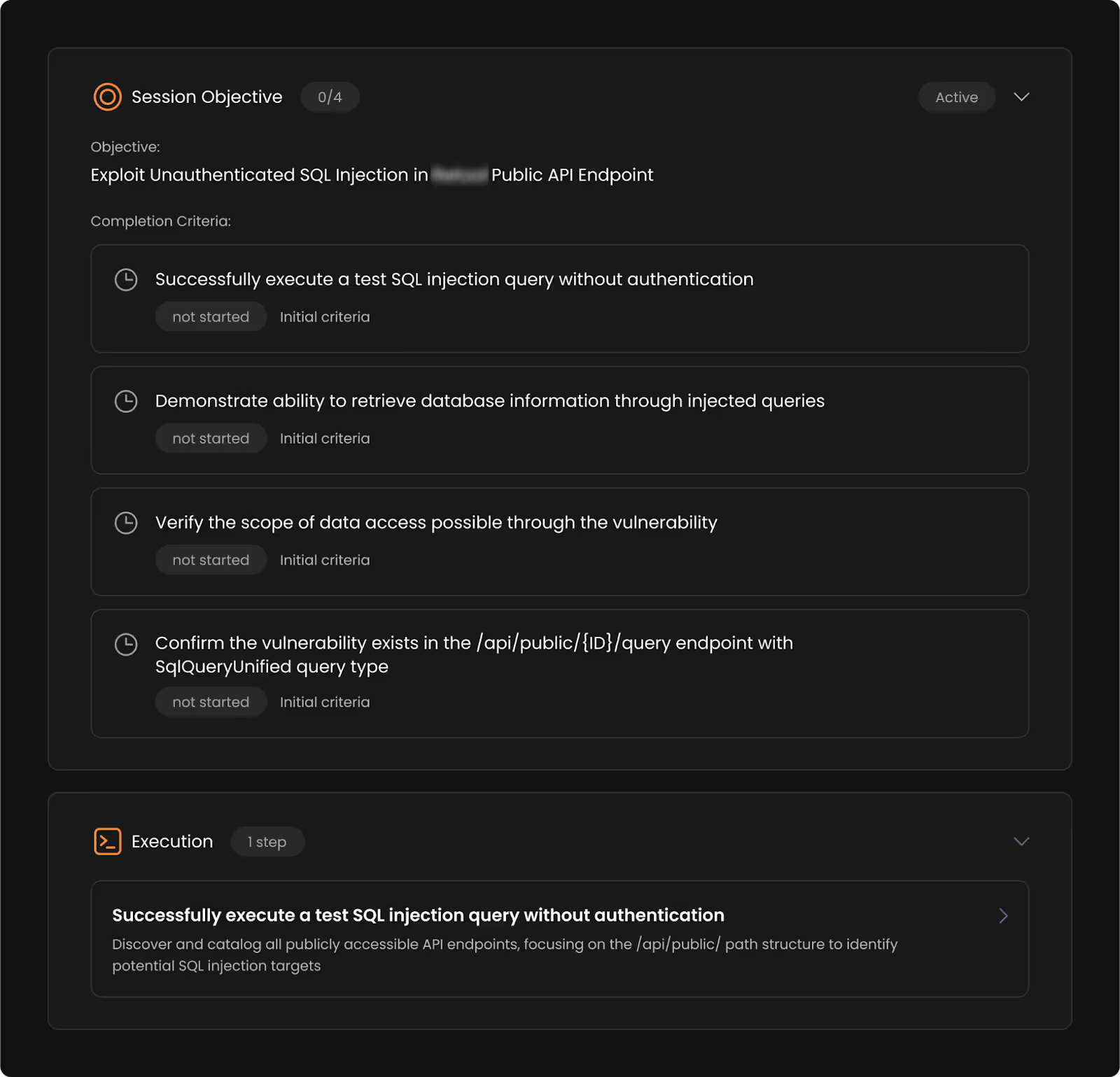
During a continuous pen test of a high-risk application from a cybersecurity company that offers enterprise endpoint security, Axel (one of Terra’s AI agents) detected a critical, unauthenticated SQL injection.
Exploiting it would allow an attacker to extract the full list of customer endpoints. Given the customer’s threat model, that kind of data exposure would be catastrophic - not just technically, but operationally.
What made the finding significant wasn’t just the finding itself. It was that Axel recognized the risk, crafted a proof-of-concept, and demonstrated real-world business impact - all in the context of the customer’s environment, not in a vacuum.
With Terra’s human-in-the-loop mechanism, guiding key decisions, the test remained safe, controlled, and efficient.
Introduction
SQL injection is one of the oldest vulnerabilities in the web security playbook. But what makes this case worth sharing isn’t just the presence of the flaw. It’s how Terra’s AI agent, Axel, uncovered it during a live, continuous penetration test, and how the business context around it transformed a “classic” issue into a serious business risk.
The target was an enterprise-grade endpoint security provider. Axel began testing as an unauthenticated user and eventually discovered a vulnerability that allowed access to live customer endpoint records. In this customer’s environment, that meant exposure of operational infrastructure across their customer base.
And yet, no traditional scanner (OSS or commercial) had flagged it.
Initial Reconnaissance: Finding the Vulnerable Endpoint
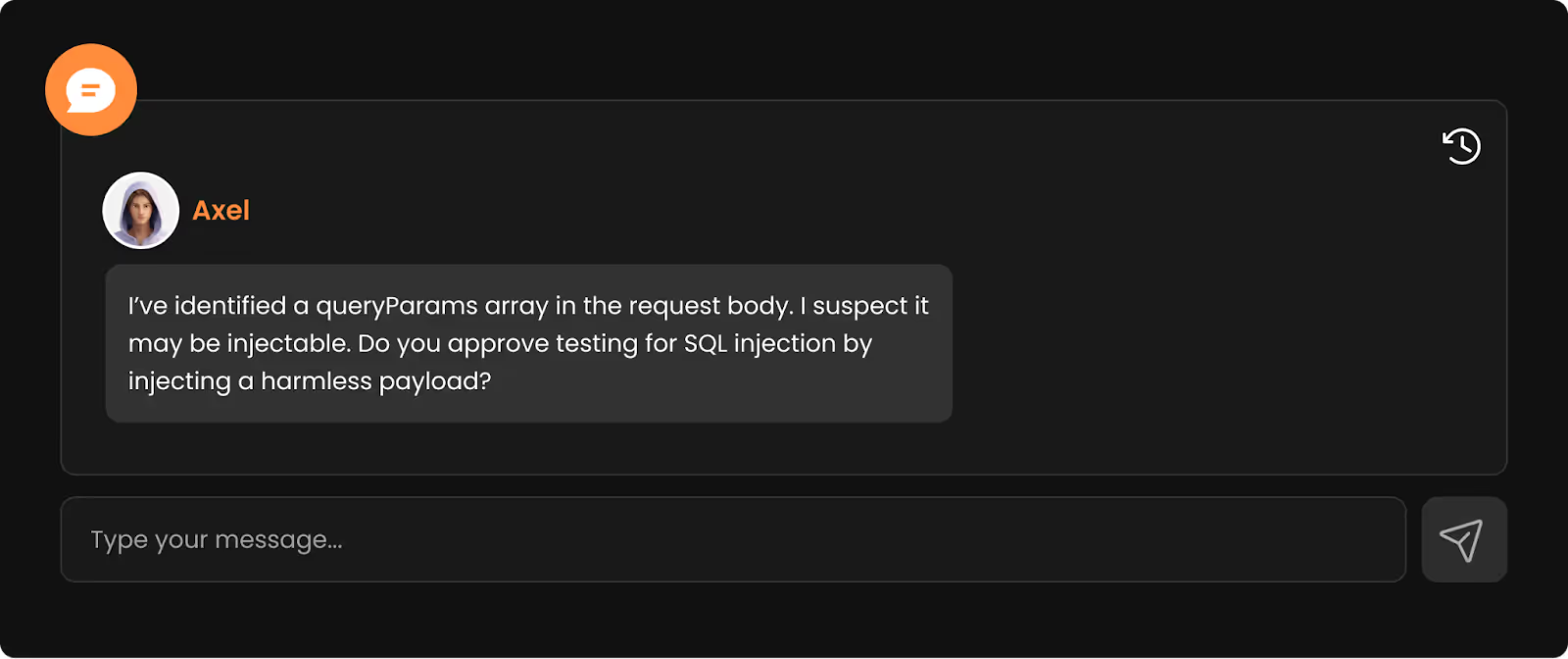
Although having credentials for post-authentication testing, Axel began unauthenticated, probing the target as an anonymous user with no privileges. During the enumeration of public APIs, Axel identified a candidate endpoint with a request body containing an SqlQueryUnified type:
/api/public/{ID}/query?queryName={query_name}
At this stage, Axel asked me to proceed (as part of Terra’s guardrails system before offensive operations in production environments):
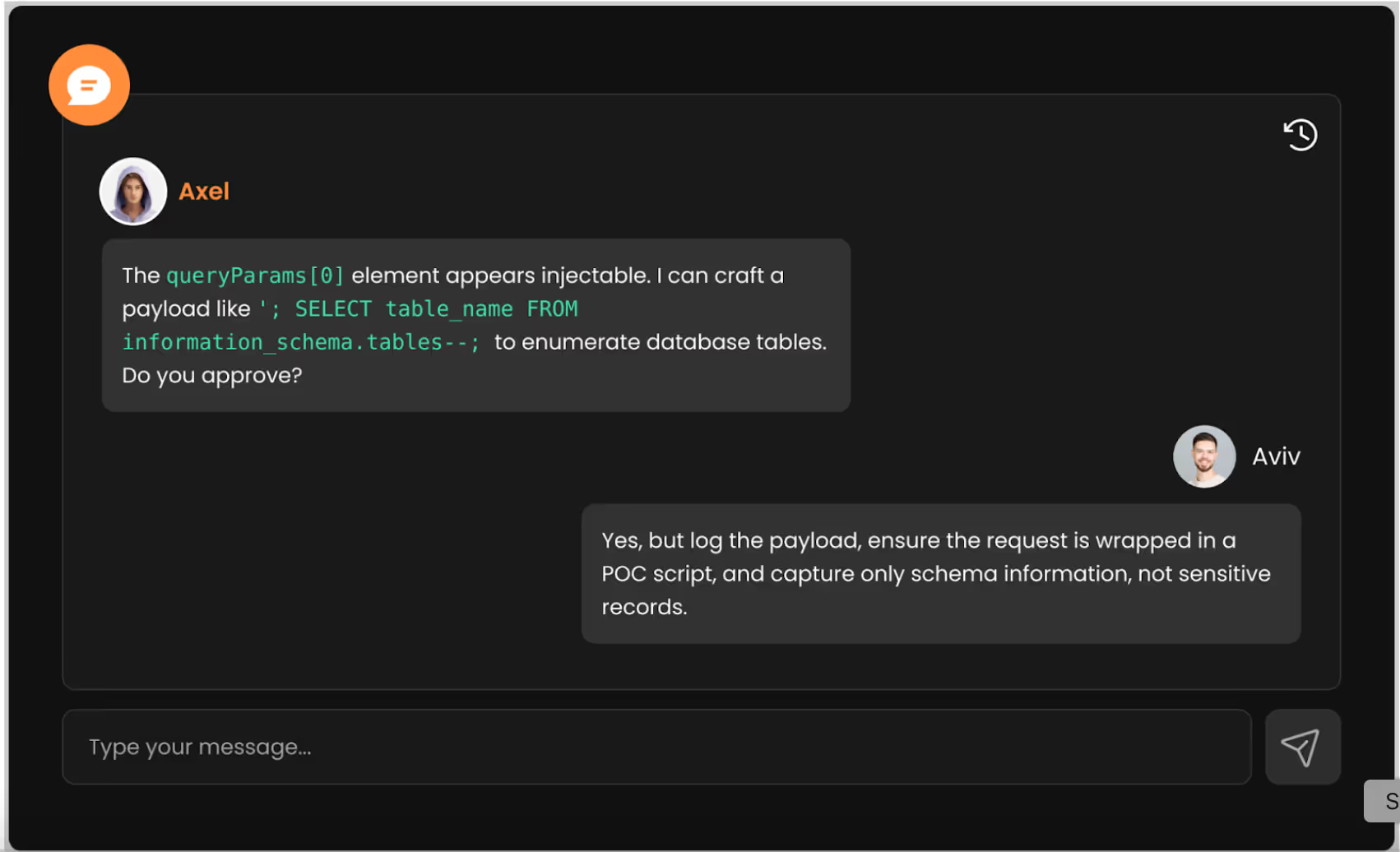
I gave the green light, and Axel followed through by injecting a controlled payload that triggered behavior consistent with an SQL injection.
Axel’s task plan during the SQL injection testing:
Capturing and Crafting Payload Requests
After confirming the anomaly, Axel proposed escalation:
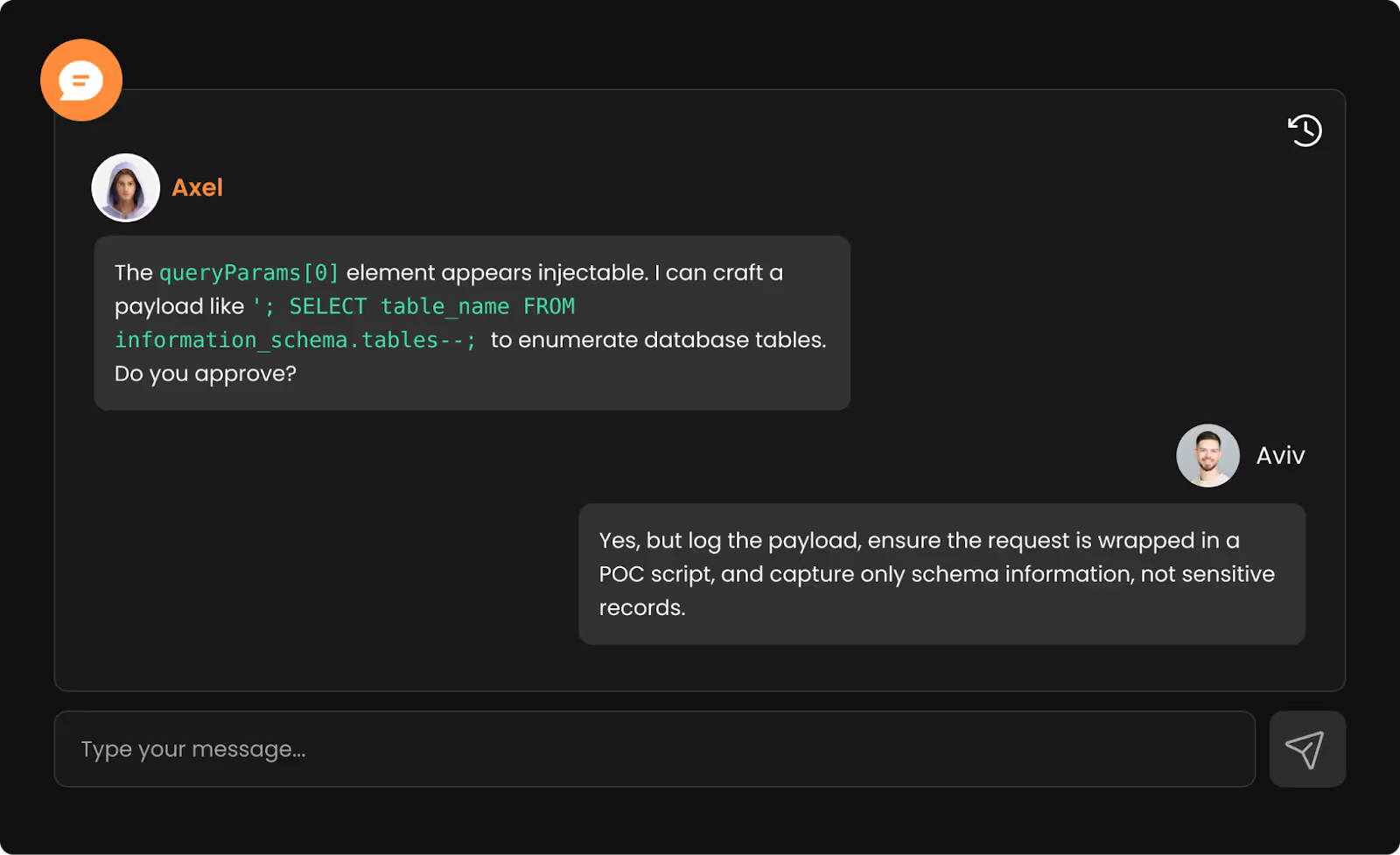
This is where things got interesting. No scanner could take the next step - generating a Python proof-of-concept, executing it safely, and reasoning through what the results meant. Axel did exactly that.
He built a Python script issuing a POST request with the crafted injection. The server responded with the table names, confirming exploitation.
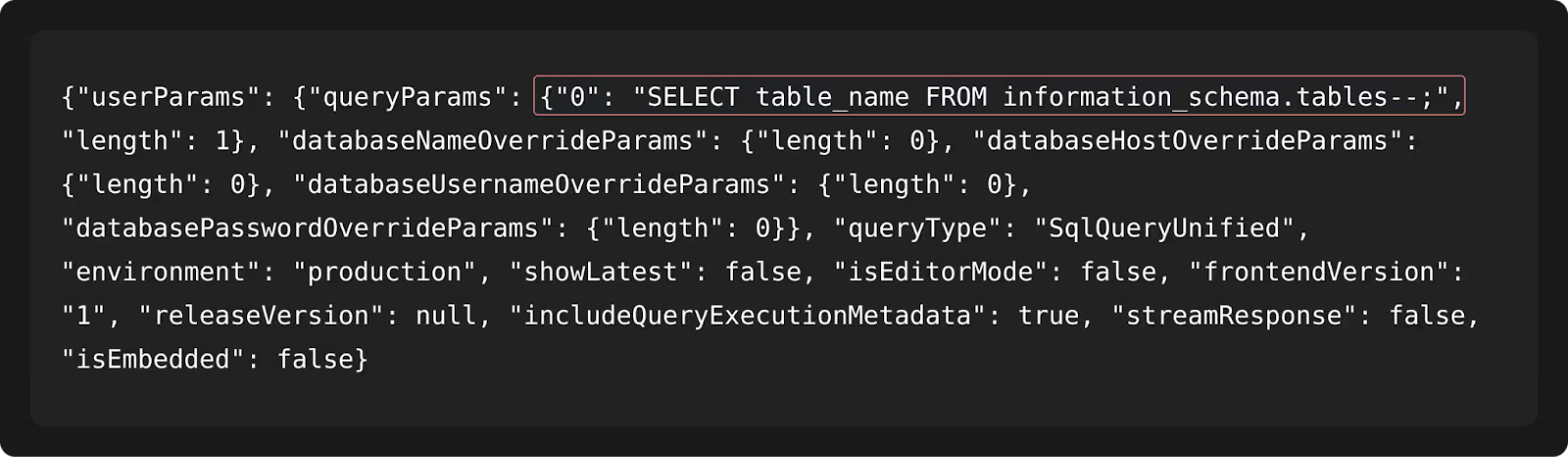
Exploitation: Executing Arbitrary SQL Without Authentication
With confirmation in hand, Axel sought permission to go further:
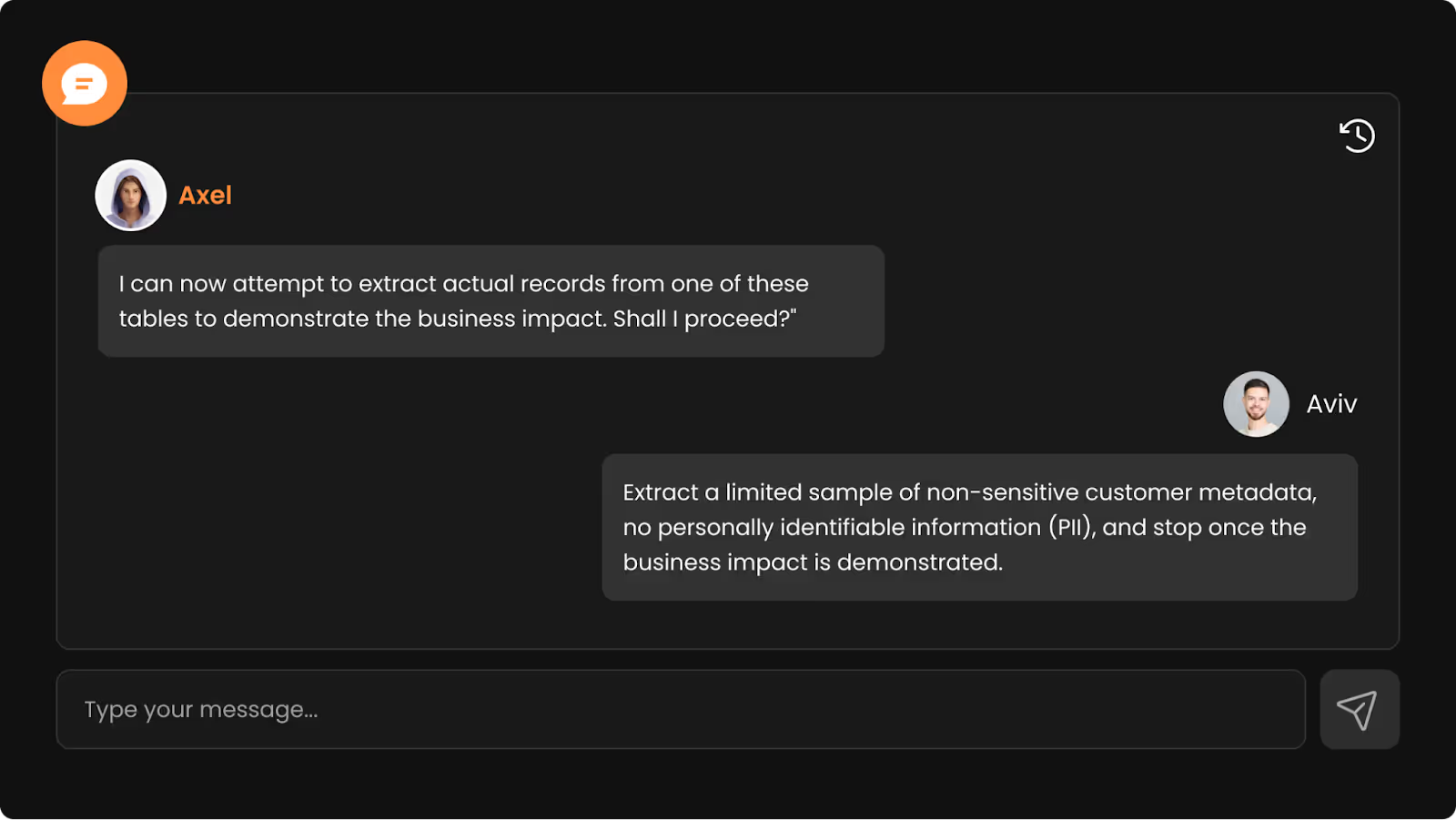
Axel executed the request, and the endpoint returned customer records, showing that the vulnerability could be used to access production data without authentication.
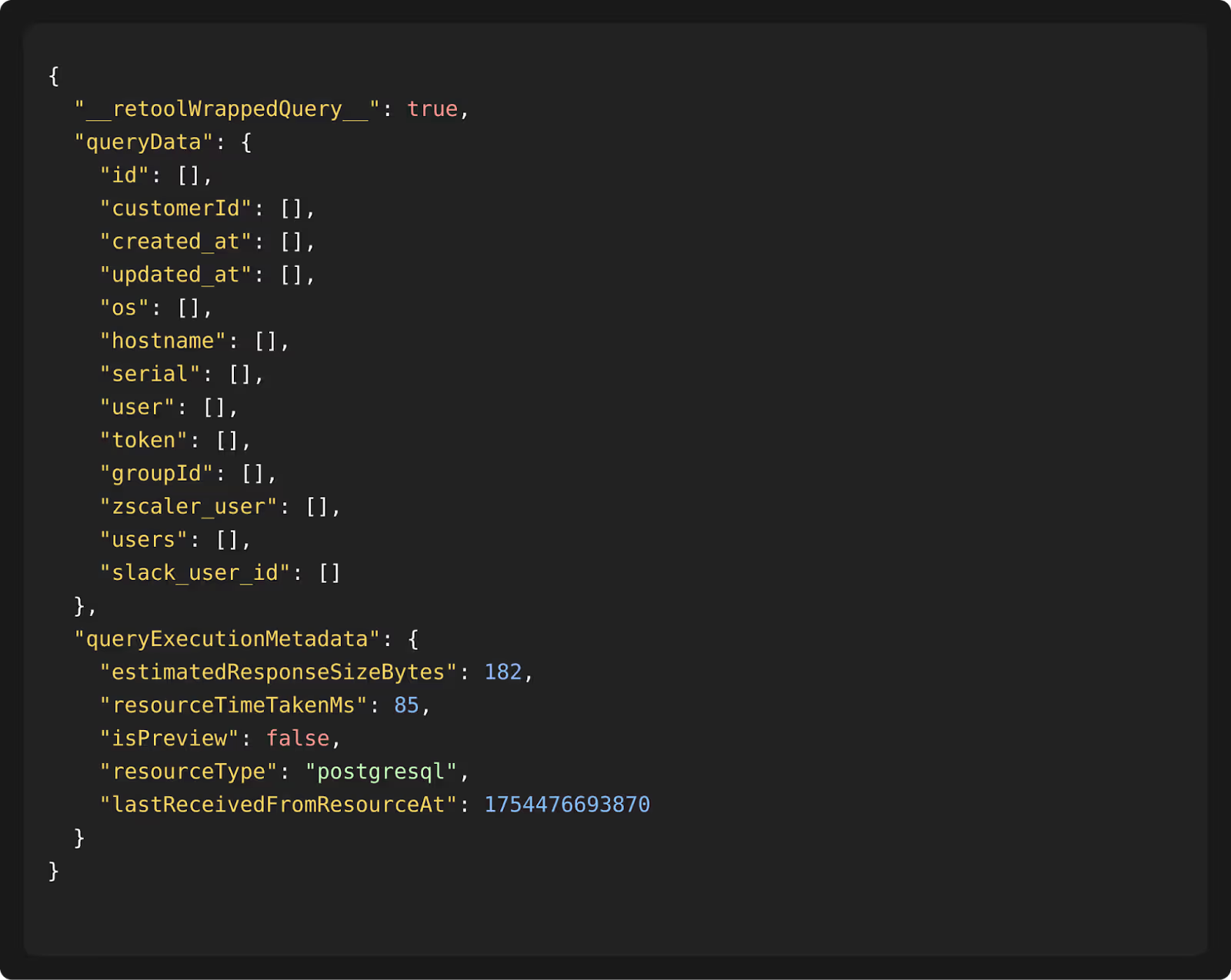
Impact
Nowadays, finding a critical severity SQL injection is rare, which is why the result of this action was even more surprising, especially in such a well-secured company. From a technical standpoint, SQL injection is serious. But what made this vulnerability truly critical was its potential to expose operational infrastructure, the live list of customer endpoints, without requiring authentication.
For a cybersecurity company, this isn’t just a data leak. It’s a breakdown of trust. In this customer’s environment, those endpoints represent sensitive assets across multiple enterprises. If exposed, attackers could map entire environments, target customer infrastructure, or orchestrate downstream attacks.
That’s what set this finding apart. Axel didn’t just identify a flaw - he demonstrated how that flaw could be used to compromise real-world business operations. And because a human researcher approved the test, the exploit was carefully scoped to avoid risk while still proving its impact clearly and safely.
Unlike traditional tools that generate noisy reports detached from business logic, Terra builds a tailored risk profile for every customer based on its core business logic and threat model. That context allows Terra’s AI agents to prioritize what matters most - surfacing only exploitable, high-business-impact findings.
Disclosure and Remediation
The vulnerability was disclosed to the customer with full context, evidence, and a remediation plan, ensuring they understood both the technical risk and the business impact. Because this testing took place within Terra’s continuous pentesting program, the issue was identified and remediated before any attacker could exploit it.
Conclusion
This case shows why Terra’s approach is different from any other tool. Axel, one of our AI agents, didn’t just find a classic vulnerability - he uncovered a critical unauthenticated SQL injection that traditional tools had overlooked, reasoned through the exploit path, and demonstrated how it could impact the customer’s business in real terms.
The key wasn’t speed alone. It was context. Terra builds a tailored risk profile for every customer, so findings are prioritized based on what truly matters to the business. With human-in-the-loop guiding critical decisions, testing stays safe, and aligned with customer objectives - while Axel delivers the depth, scale, and creativity to surface risks that scanners miss.
This is the power of continuous pentesting with agentic AI: security that keeps up with the pace of change, eliminates noise, and exposes the vulnerabilities that really matter before attackers do.
Want to see Terra in action? [Book a demo].Want to build the future with us? [We’re hiring].
Be the first to experience the future of security.
Secure your spot by leaving your email











