Back
How to Execute a White Box Penetration Test: Step-by-Step Guide

Modern web apps move fast, but speed alone isn’t enough. Like a Formula 1 team tuning every component under the hood, white box penetration testing delivers complete visibility into the application’s inner workings. With complete access to code and architecture, it enables precise, high-impact tests that catch vulnerabilities other methods miss.
And the risks of missing these vulnerabilities have never been greater. As of early 2025, app-focused attacks surged to 83% of all cyber incidents, up from 65% the year before. Legacy pen testing approaches fail to keep up with this pace.
White box penetration testing ensures that vulnerabilities are understood within their business context and fixed before they become breaches. For CISOs and security leaders, it’s not enough to know that white box testing is valuable; it’s essential to understand how it works in practice and what to demand from a provider.
What is a White Box Penetration Test?
A white box penetration test is software testing performed with the assumption of full internal knowledge, where the testers have access to the source code, architectural diagrams, and credentials.
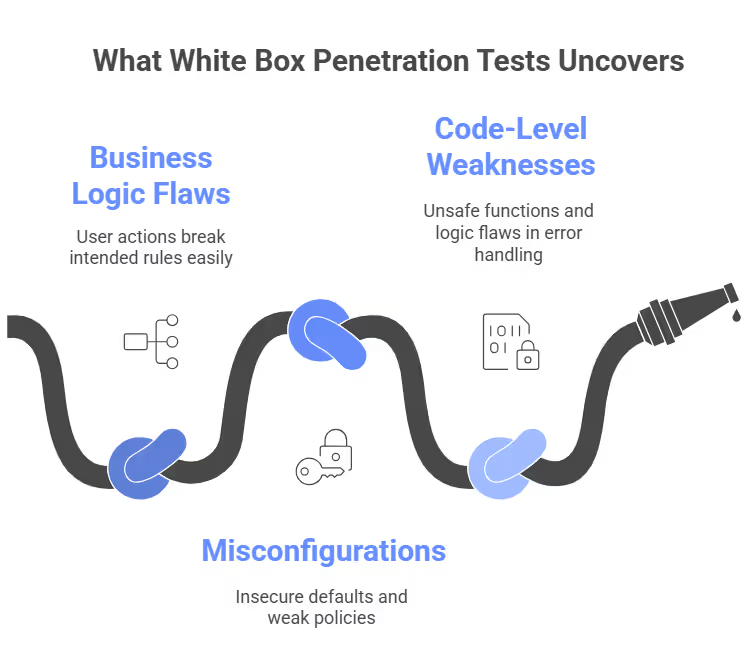
White box penetration tests are a logical continuation of QA using other means. The “insider perspective” enables testers to examine the application thoroughly. This includes rarely used logic paths and interconnected dependencies. This kind of deep access means white box testing is particularly effective at uncovering vulnerabilities often missed by automated scanners or gray/black box testing. These include:
- Business logic flaws - situations where valid user actions can be sequenced or structured in a way that breaks intended rules.
- Misconfigurations - insecure defaults, exposed secrets in code, or weak API authorization policies.
- Weaknesses at the code level - unsafe functions or dependencies, cryptographic errors, and logic flaws in error handling that attackers could exploit.
Within offensive security, penetration testing is one of the core practices, and it can be carried out using white box, black box, or grey box approaches. White box testing typically involves following the path of sensitive data or attempting to reroute or manipulate sensitive processes, such as transactions. Because grey and black-box testing lack this internal knowledge and visibility into business logic, they often miss these deeper vulnerabilities. Here are the key differences between the three testing types:
- Black-box testing: Mimics an external attacker without knowledge of the system or access to its internal functionality. The application logic coverage is limited since you can only test the exposed surfaces.
- Grey-box testing: The testers have partial knowledge of the system but usually get credentials to access the post-authentication functionality. This testing type attempts to balance white and black testing, but still misses deeper logic flaws.
- White-box testing: Attacks have full knowledge of the system before the test and can validate internal code paths and logic flows. This is the only model that finds vulnerabilities deep in the business logic or code.
How to Execute a White Box Penetration Test: Step-by-Step Guide
Step 1: Scoping & Context Building
The first step in almost any testing is defining the scope and desired context of the test. Start by determining the business-critical paths and workflows that align with your app's business logic. Some examples include the authentication and authorization logic, integrations, transactional flows, and critical API calls. Potential attackers seek to disrupt and abuse your app, not just ‘get in’. If broken, these paths could break your app, enable unscoped behaviour, or allow for sensitive data exfiltration.
Step 2: Information Gathering
After defining the scope, the next stage is collecting intelligence on possible weaknesses in the code base and internal assets. This includes reviewing error-handling routines, configuration files, API endpoints, and third-party dependencies, particularly open-source components.
Dependency mapping is central to this process. Today’s applications rely on sprawling software supply chains, with layers of libraries, external services, and integrations. If left unmapped, these links can conceal serious risks. A single outdated package or a poorly secured API endpoint can open the door to attackers, enabling lateral movement and deeper compromise across connected systems.
White box testers can review these components in detail to flag outdated libraries, insecure defaults, or overexposed internal APIs before attackers abuse them. Testers often automate static application security testing (SAST) tools to analyze code for insecure functions, cryptographic flaws, or logic errors. Combined with dynamic analysis (DAST) on running builds, this dual approach highlights structural weaknesses in the code and behavioral flaws in a running test environment.
Step 3: Attack Surface Mapping
White box testing should be performed with full access to every shred of relevant data and records. However, the gaps in documentation and developer oversight may create “shadow assets” that will not be available to your testers. Use a discovery tool to find every potential asset and access point through which a user or attacker might gain entry to your application. Nmap is considered one of the better free tools for this task.
Once you have identified your exposed attack surfaces, ensure they align with the business logic. Such exposed surfaces include APIs, third-party service connections, database interfaces, and login or permission screens. This is especially critical, since dormant or undocumented APIs may allow attackers to disrupt your app or steal your users’ information. Instead of treating every endpoint equally, testers can identify “choke points” where a single exploit cascades and escalates across the environment.
White-box testing is the only approach that can promise to cover your entire web attack surface.
Step 4: Test Execution
In this stage, testers move from planning to active exploitation. Using the knowledge gathered in earlier steps, they explore privilege escalation through compromised credentials, misconfigured session tokens, or weak password recovery mechanisms.
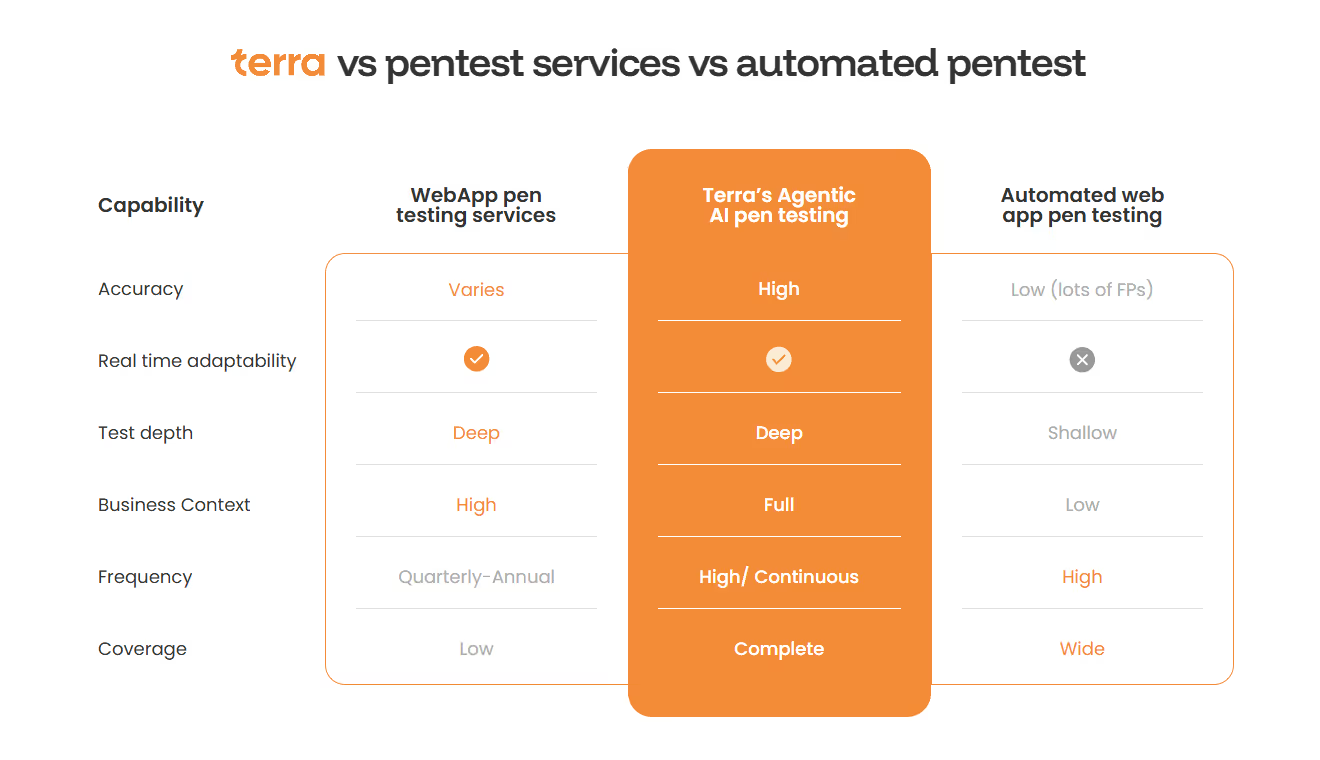
Traditional white box penetration testing is manual, slow, and inconsistent. Skilled testers may uncover complex vulnerabilities, but manual execution is resource-intensive, varies in quality, and cannot keep pace with fast-moving applications. Automated scanners provide broad coverage but are superficial and noisy, often missing the deep, logic-driven flaws that matter most.
What’s needed is business-contextualized testing, an approach that understands how vulnerabilities intersect with each application’s unique workflows, users, and risk model. Terra deploys a swarm of AI agents that simulate the reasoning of skilled human testers, adapting in real time to your application’s unique logic and risk profile continuously and at scale.
Because these agents never tire, they can cover more attack paths simultaneously. Meanwhile, a human-in-the-loop element validates critical findings and guarantees accuracy and safety. The result is a testing process combining the accuracy and business-logic depth of manual pen testing with automation's speed, adaptability, and breadth.
Step 5: Reporting and Remediation
Once testing is complete, the results must be presented to stakeholders, including security leadership such as the CISO, compliance officers, engineers, and product owners, with in-depth context and actionable insights. A penetration testing report template should cover, among other things, detailed findings and context, prioritization levels, suggested remediation steps, and context-driven, compliance-ready reporting outputs.
When it comes to risk prioritization, consider aligning it with three axes; the higher the score on all three, the more critical the issue:
- Business impact - how exploitation would affect operations, revenue, or compliance.
- Exploitability - how easily an attacker could weaponize the flaw.
- Remediation readiness - whether fixes can be implemented without breaking the existing production systems.
It’s also essential to provide R&D teams with detailed remediation guidance to mitigate the issues discovered in the testing phase without impacting development velocity. The recommendations may include suggesting safer functions, dependencies, or different API call structures.
Top Challenges in Performing a White Box Penetration Test
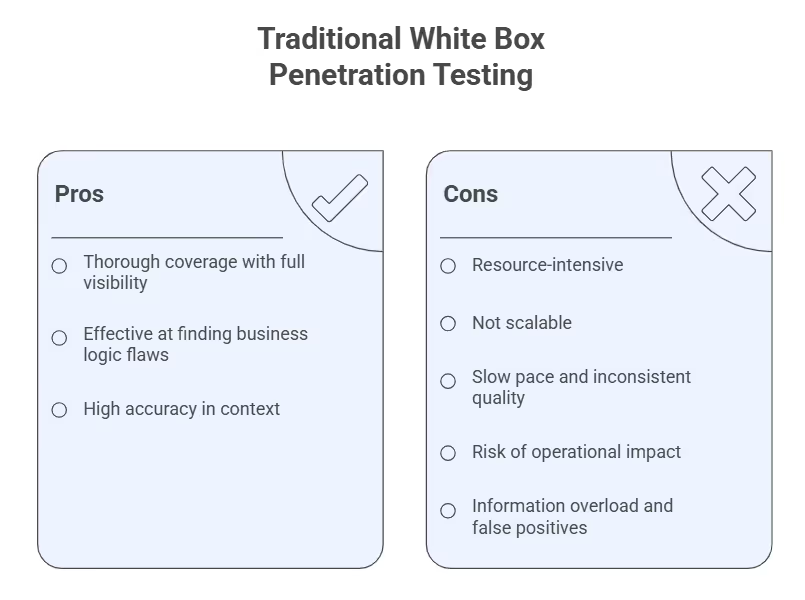
Although white box penetration testing is the most thorough way to assess application security, it has challenges. We have touched on some of these earlier, but here’s a comprehensive list of limitations, followed by how to overcome these:
- High expertise required - Interpreting source code, business logic, API scores, and data flows demands deep technical knowledge. Many organizations lack in-house expertise to identify subtle code-level issues or logic flaws, and even external pen test providers often fall short, relying on automated scans or checklist approaches instead of accurate white box analysis.
- Data overload - Full visibility often generates an overwhelming amount of information. Without effective filtering and prioritization, security teams can end up drowning in information and findings that obscure the most critical risks.
- Risk of production impact - If poorly scoped or executed, tests or fixes may interfere with live production systems, risking downtime or data corruption. This makes careful planning, sandboxed execution, and pre-deployment testing environments critical for safe testing, especially when working with business-critical systems.
- Business logic complexity - Some of the most dangerous vulnerabilities arise not from coding errors but from flaws in application logic. Detecting these requires creativity, a nuanced understanding of workflows, and deep coding and business logic knowledge.
- Full disclosure bias - Since a white box test requires full disclosure, testers might wrongly assume they should focus exclusively on the information provided. However, security teams have probably gone over the known attack surfaces and workflows with a fine-tooth comb, so it is the tester's job to miss what developers and security teams missed.
What You Need for an Effective White Box Penetration Test
Because white box testing provides full disclosure, it can quickly overwhelm testers and organizations. The volume of code, configurations, and business workflows is enormous, and without the right approach, teams risk missing critical issues or drowning in noise. To be effective, a modern white box test should incorporate several best practices:
- Balance automation with human expertise - Automation is invaluable for breadth, but human creativity and contextual reasoning are essential for uncovering business logic flaws and multi-step exploit chains.
- Prioritize findings by business impact - Raw vulnerability lists often paralyze development teams. Risks should be triaged by exploitability, potential damage to operations or compliance, and ease of remediation.
- Adapt dynamically - A good tester adjusts their approach as new findings emerge. Testing that cannot adapt risks missing the vulnerabilities that matter most.
- Ensure safe execution - With access to internal systems, poor scoping or reckless testing can disrupt production. Guardrails, sandboxing, and oversight are key.
Agentic AI solutions provide unique value because they simulate how skilled attackers adjust their strategies in real time, extending human intuition with scalable, tireless exploration. Terra’s approach combines these adaptive AI agents with human-in-the-loop oversight to ensure safe execution, eliminate false positives, and focus remediation on the issues that reduce real business risk.
Racing Ahead of Threats
A Formula 1 car isn’t just driven fast; it’s engineered for resilience. Every system is tested, retested, and stress-modelled to withstand extreme conditions. Penetration testing follows the same principle: with white box access, security teams can inspect systems at depth, identify weak points, and harden them long before real-world pressure reveals the cracks.
That’s the value of white box penetration testing. With complete visibility into an application's code, architecture, and configurations, it goes beyond surface scans to uncover issues that matter most: broken business logic, API exposures, and vulnerabilities buried deep in the stack.
Terra extends this approach with its agentic-AI platform. Think of it as a pit crew that never steps off the track - combining the scale and persistence of AI with the judgment of seasoned testers. The result is continuous coverage, prioritization based on real business impact, and expert oversight that helps enterprises stay ahead of evolving threats.
Book a demo to see how it works.
Be the first to experience the future of security.
Secure your spot by leaving your email








