Back
Red Team vs. Penetration Testing: Which Service Do You Need?
.avif)
No matter the tests you are running, the absence of a breach can no longer be considered a sufficient and satisfactory result by itself. Boards and regulators now expect measurable return on investment: proof that testing reduces risk, strengthens compliance, and drives efficiency.
Security budgets may be growing, but so is the pressure. In 2024, average budgets increased by 8%, with only 12% of CISOs facing cuts. With higher spending comes higher expectations, and the risk and cost of a potential breach have never been greater.
The introduction of AI-based solutions for penetration testing has flipped the script and made the traditional, seemingly dichotomous yet complementary relationship between pen testing and red teaming seem outdated. But before discussing the future of pen testing and red team, we must first understand how these practices have evolved.
What is Red Teaming?
Red teaming is an advanced offensive security exercise designed to test an organization’s resilience by emulating real-world adversaries. Unlike traditional penetration tests, which focus on cataloging vulnerabilities, red teams use tactics such as phishing, malware deployment, supply chain compromise, and lateral movement to pursue far-reaching objectives.
The goal is to evaluate how well people, processes, and technology work together to detect, contain, and respond to a live intrusion. To preserve realism, only a handful of stakeholders know the drill is underway.
This made red teaming fundamentally different from internal or external penetration testing. Where pen tests used to culminate in a report of vulnerabilities, red teaming answered broader strategic questions:
- Would our SOC detect a stealthy breach?
- Could incident response contain credential theft?
- How would leadership react to a ransomware event?
However, today, agentic-AI powered pen tests are changing the way we look at offensive security as a whole, and specifically red teaming and pen testing. Agentic testing offers many of the same capabilities once limited to manual red team operations. Intelligent agents can simulate sophisticated attack chains, adapt to their environment, and perform dynamic, context-aware assessments. Over time, these AI agents learn and improve, delivering increasingly accurate evaluations that mirror real-world adversaries' tactics, techniques, and procedures (TTPs), at scale and continuously.
The value of this approach was underscored in late 2024 when CISA red-teamed a US critical infrastructure provider. Simulated attackers went undetected for months, exposing technical gaps and breakdowns in communication and executive response - proof that resilience testing matters as much as vulnerability discovery.
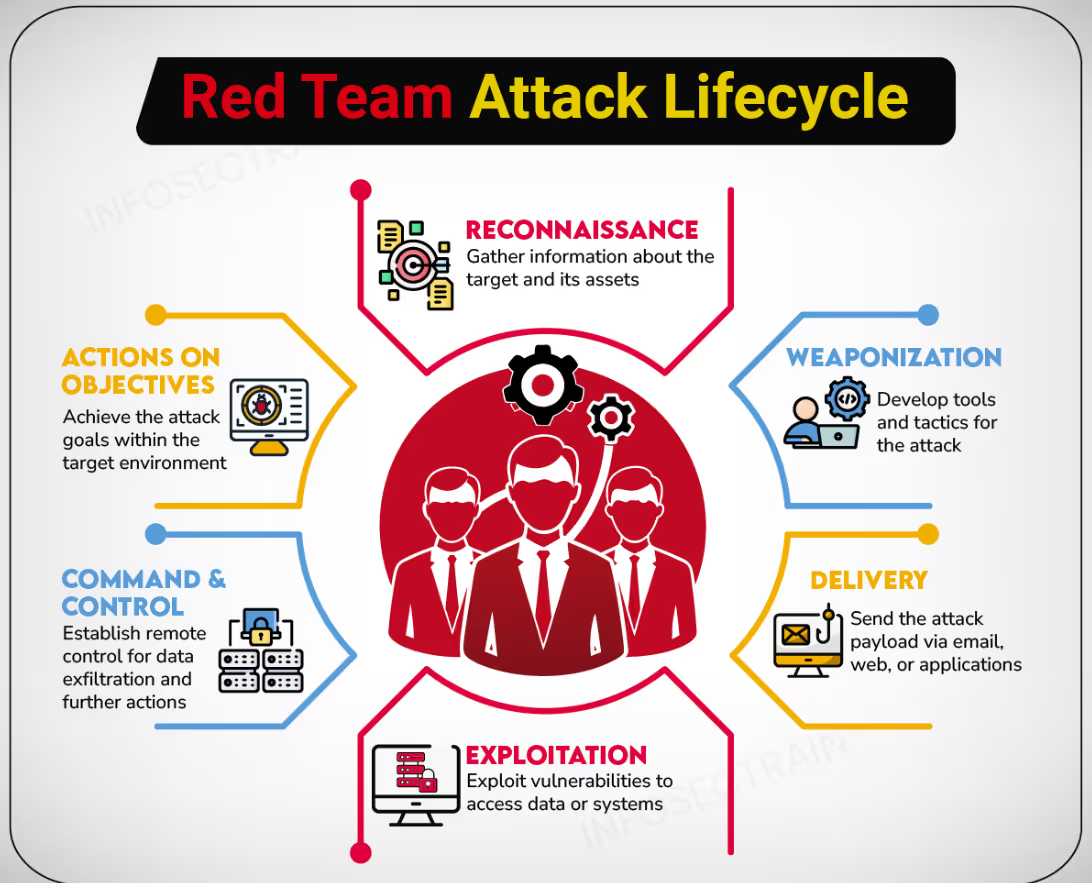
Red Teaming Is Used For:
- Advanced threat simulation - Simulates various adversaries, such as nation-states or ransomware groups, to reveal how an organization would fare against today's deadliest campaigns (this can now also be achieved with AI pen testing solutions).
- SOC maturity testing - Verifies whether the security operations center can detect and contain intrusions across various attack vectors in real-time.
- Resilience validation - Tests the entire defense chain, from technical controls to human decision-making under duress.
- Executive readiness - Presents boards and leadership with real-world insights into business continuity risks, making cybersecurity an enterprise priority.
Red teaming clearly shows companies their actual level of readiness. It narrows the theory-to-practice gap, ensuring investments in tools and processes deliver tangible resilience when facing today's adversaries.
What is Penetration Testing?
Penetration testing was a controlled assessment of systems, applications, or networks that uncovers vulnerabilities before attackers can exploit them. Unlike red teaming, which emulates a full-scale adversary campaign, traditional or legacy pen testing is narrower in scope and purpose-driven: it identifies, confirms, and documents weaknesses so your team can remediate them before adversaries can exploit them.
A typical traditional pen test engagement follows a structured process of scoping, intelligence gathering, exploitation, and reporting. The outcome is tangible: a report detailing vulnerabilities, proof-of-concept exploits, and remediation guidance. This makes pen testing valuable for compliance audits, stakeholder assurance, and secure development practices.
Penetration Testing Is Used For:
- Securing development cycles - Pen tests supplement DevSecOps pipelines by preventing new releases and updates from containing exploitable vulnerabilities.
- Discovery of exploitable vulnerabilities - Goes beyond automated scan by safely exploiting threats to prove real-world impact and prioritize patches.
- Third-party assurance - Provides customers, partners, and regulators with written confidence that security testing is continuous and effective.
- Compliance requirements - PCI DSS 4.0 requires annual and change-triggered penetration tests and periodic segmentation tests. SOC2 can be replaced with FedRAMP, which requires pen testing at least annually.
Legacy pen testing has its downsides: It is generally a one-off, capital-intensive exercise, and it can’t keep up with the rapid pace of development of high-velocity cloud-native environments. That is why numerous CISOs are increasingly shifting towards AI-powered penetration testing platforms that offer continuous, robust, quality, business-logic-sensitive testing.
Such platforms leverage the power of automation and human insight to minimize noise, scale across hundreds of apps, and make actionable suggestions, plugging security and compliance gaps while staying current with risk exposures.

Red Team vs. Penetration Testing: The Key Differences
Although frequently referenced together, red teaming and penetration testing exist to solve different questions. However, modern pentesting can perform much of what red teaming used to do, as it utilizes AI agents that work continuously to simulate adversaries at scale. The following is a breakdown of how the two strategies compare regarding significant dimensions.
1. Primary Goal
- Pen Testing: The primary goal was to discover and exploit vulnerabilities within a specified scope, presenting a ranked list of vulnerabilities to fix. These days, AI agents can also successfully simulate real-world adversaries and cover a much broader attack surface than the traditionally limited pen test.
- Red Teaming: The aim is to test organizational resiliency. Not just technical vulnerabilities, but also people's readiness, detection, and response.
2. Scope
- Pen Testing: Typically limited to individual systems, applications, or environments (e.g., a web app or cardholder data environment for PCI DSS). With AI agents, these limitations are a thing of the past, and modern pentesting can cover multiple systems and apps with no scaling issues.
- Red Teaming: Flexible and open, designed to mimic an attacker's mindset against the whole organization, often without limits.
3. Methodology
- Pen Testing: The legacy pen test procedures follow formal stages such as scoping, reconnaissance, exploitation, and reporting within predefined standards (like OWASP top 10, NIST 800-115, or ASVS). Agentic-AI pen testing emulates real-world adversaries far better than the traditional pen test. It could also be closer in style to red teaming.
- Red Teaming: Emulates the tactics, techniques, and procedures (TTPs) of real attackers, often involving multiple attack vectors (social engineering, phishing, malware, lateral movement).
4. Duration
- Pen Testing: traditionally short tasks, usually 1-4 weeks. Modern, continuous pen testing is far more suited to the fast pace of modern development and adversary advancement.
- Red Teaming: Long-running campaigns, weeks or even months, to simulate persistent attackers.
5. Deliverables
- Pen Testing: Technical report of vulnerabilities. The pen test report template includes vulnerabilities that attackers can exploit, their risk factors, and remediation recommendations. Traditionally, penetration testing resulted in a single technical report. Today, platforms can connect directly to your organization’s stack (such as Slack, Jira, or Splunk) and display findings in a live dashboard for continuous visibility and remediation tracking. Customers can still get formal reports annually for compliance and audit purposes.
- Red Teaming: Narrative report illustrating attack vectors, how attackers progressed, if the attack methods were detected, and the organization's response.
6. Focus Areas
- Pen Testing: Reveals technical vulnerabilities such as SQL injection, IDOR, misconfigurations, and access control vulnerabilities. AI agents that simulate real-world adversaries can also reveal complicated changed vulnerabilities that could lead to a system penetration or takeover.
- Red Teaming: Exercises people, processes, and technology together, often emphasizing where incident response, monitoring, or decision-making by leaders falls short.
7. Attack Surface
- Pen Testing: Traditionally, pen testing was scope-limited and narrowed to a few applications or environments (an average of ~7% of the attack surface). Agentic-AI expands that reach, automatically discovering and testing interconnected components such as subdomains, authentication flows, and third-party integrations.
- Red Teaming: Uninhibited, any attack vector a realistic adversary might use, from phishing staff to breaching through the company’s network.
8. Use Cases
- Pen Testing: Legacy pen testing was most appropriate for compliance (PCI DSS, SOC 2), secure software development assurance, and discovering exploitable vulnerabilities in critical assets. Agentic-AI-powered pen test approaches aim to help the organization build a robust, verified security program that covers the modern development lifecycle, speed, and continuous search for exploitable vulnerabilities.
- Red Teaming: Most appropriate for simulating advanced attacks, assuring SOC maturity, and preparing executives for real-world crises.
9. Cost and Resources
- Pen Testing: Cheaper, but generally needs to be repeated regularly to remain helpful in changing environments. Continuous pen testing, however, can cover every change in the attack surface and the environment it’s run on in a much more cost-effective way than a point-in-time pen test engagement.
- Red Teaming: Cost- and internally coordinating-intensive, but yields strategic lessons traditionally greater than technical vulnerability identification.
10. Who Benefits Most
- Pen Testing: A good fit for organizations of any maturity level that need point-in-time assurance, particularly those driven by compliance or limited resources. With the rise of AI-driven and agentic platforms, pen testing has evolved into a continuous, adaptive process that benefits a broader range of organizations, from fast-moving SaaS companies and digital retailers to complex enterprises managing large web ecosystems.
- Red Teaming: Best suited for mature organizations with robust defenses that want to measure real resilience versus advanced threats.
How to Choose the Right Service for Your Organization
Choosing between red teaming and penetration testing is a strategic decision shaped by your organization’s security maturity, risk tolerance, and regulatory obligations. In reality, the two aren’t competing approaches but complementary ones. For a truly resilient security posture, it’s best to incorporate both at different stages of your program for a truly resilient security posture. Here’s what to consider when determining the right balance:
- Maturity matters. Small or medium-sized organizations will gain the most from penetration testing, which verifies secure development and compliance. Meanwhile, large organizations with established defenses should now have vulnerability control as they employ continuous pentesting. They might require red teaming to test how proficient their security operations, processes, and leadership are against real-world attack simulations.
- Compliance vs. resilience goals. If you must pass audits and demonstrate security to regulators, continuous penetration testing provides the systematic, repeatable results you need (it doesn’t have to be continuous, but it is recommended). If your challenge is preparing your people and processes to handle advanced attackers or validating incident response preparedness, red teaming provides greater strategic insight.
- Risk tolerance and budget. Penetration testing is less costly and easier to schedule on a regular cycle or set to work continuously. Red teaming, by contrast, demands greater investment: it is resource-intensive, time-consuming, and requires coordination across multiple departments. Therefore, only organizations with sufficient budget and appetite for the operational disruption of a live-fire exercise would typically pursue it.
There is a gap in real-world security assurance. Penetration testing highlights vulnerabilities and exploits but does not measure an organization's response to an active attack. Red teaming provides that stress test but is costly, resource-intensive, and often out of reach for younger organizations. CISOs are left between two extremes: pen testing, which could be too narrow, and red teaming, which is too advanced. Neither offers continuous, business-logic-aware protection on its own.
Solutions like Terra’s agentic-AI, continuous pen test platform blend the scalable, compliance-ready outputs of penetration testing with the creativity and depth of red teaming. Human-in-the-loop validation ensures accuracy, control, and deep business logic, while automated, ongoing coverage eliminates the limitations of point-in-time tests. The result is an increased ROI approach that delivers both actionable vulnerability findings and adversary-level attack realism, giving security teams the best of both worlds.
Finding the Right Balance
As we have seen, red teaming and penetration testing are quite different testing methods. Pen testing finds and confirms vulnerabilities in defined scopes, whereas red teaming assesses whether your people, processes, and technology will withstand actual attackers. Both are useful, and the right choice relies on your firm's maturity, compliance needs, budget, and risk tolerance.
Terra Security combines red team–style adversary agility with agentic AI penetration testing and human-in-the-loop quality control. It delivers continuous, context-aware testing that surpasses the constraints of typical pen testing services. Organizations get compliance-report-ready outputs, actionable, prioritized vulnerability guidance, and a resilient pen test program in a scalable, robust model.
Whether your goal is to pass audits, strengthen resilience, or achieve both, Terra provides a smarter way forward. Discover how Terra can transform your offensive security program.
Be the first to experience the future of security.
Secure your spot by leaving your email








