Back
Top 10 DAST (Dynamic Application Security Testing) Tools for 2025
%20Tools%20(1).avif)
Security leaders are facing a paradox. You have more tools than ever, but less certainty about which ones reduce business risk. Legacy dynamic testing platforms produce thousands of alerts, yet attackers only need a single exploitable flaw to cause significant business harm
Meanwhile, the gap between development speed and security rigor is widening. 81% of developers knowingly ship vulnerable code, and, alarmingly, fewer than half use foundational tools like DAST or other dynamic scanning to mitigate risks.
Dynamic Application Security Testing (DAST) tools’ promise is to help uncover the growing number of vulnerabilities in running applications. Still, most have failed to live up to that promise and have provided a large false positive number without uncovering deep, meaningful vulnerabilities.
However, not all tools approach this problem the same way, and since the introduction of Agentic AI, some startups have been pushing to redefine what modern DAST should deliver.
What Are DAST Tools?
Dynamic Application Security Testing (DAST) refers to tools that test live, running applications for vulnerabilities. Unlike Static Application Security Testing (SAST), which analyzes code before deployment, or Interactive Application Security Testing (IAST), which monitors apps internally, DAST operates externally, simulating how an attacker would probe a site in production.
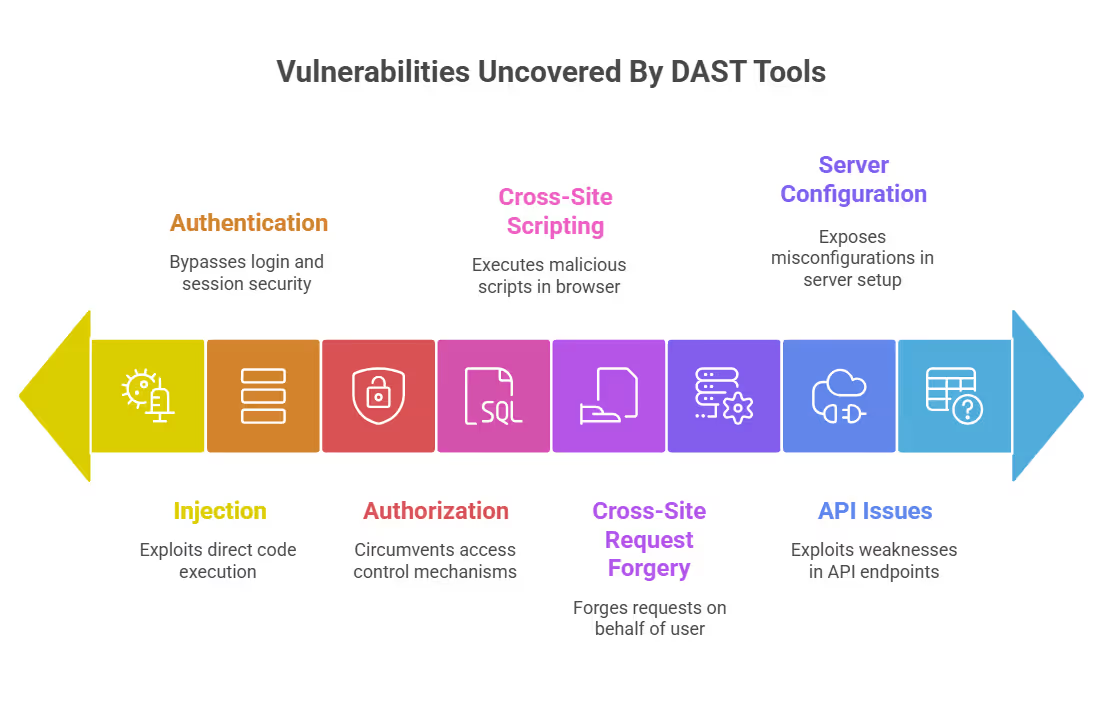
DAST sends crafted requests to a running application and analyzes the responses to identify exploitable weaknesses. It detects vulnerabilities that only appear during execution, which static testing often misses. Examples include cross-site scripting (XSS), SQL injection, insecure session handling, and broken authentication flows.
However, traditional DAST has failed to become a widely used and successful security solution.. Automated scanners tend to generate large volumes of false positives, lack awareness of business logic (for example, how a checkout workflow could be manipulated), and often provide only surface-level coverage.
This shallow detection leads many CISOs to supplement DAST with manual penetration testing, which is more in-depth but costly, slow, and complex to scale across hundreds of applications. It isn’t a question of DAST vs. penetration testing, as both methods are needed. The priority is to choose tools that minimize noise, prioritize exploitable risks, and align with business outcomes.
Benefits of Using DAST Tools
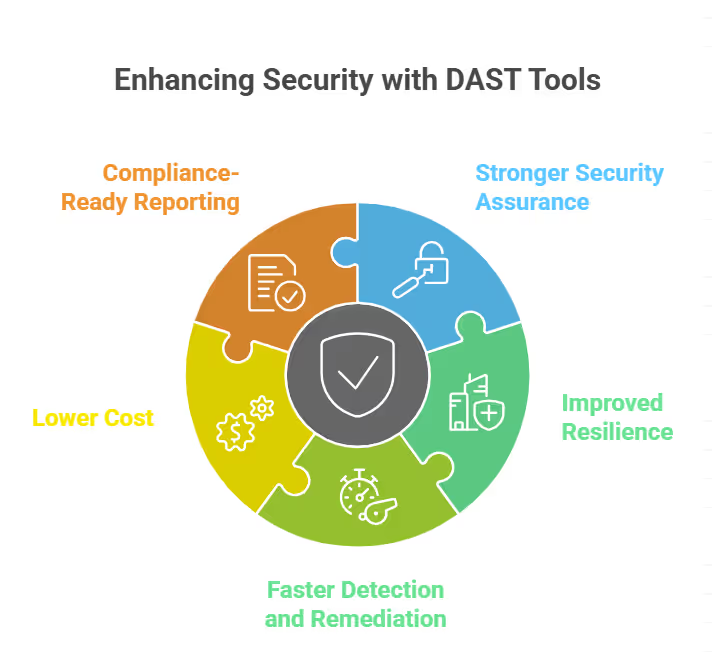
1. Improved Resilience Against Modern Attack Methods
Attackers increasingly use automation and AI to discover and exploit vulnerabilities faster than many security teams can respond. DAST helps close that gap by enabling frequent scans to detect exploitable flaws before they are widely weaponized. With recent advances in AI agent security, some tools are beginning to adapt scanning strategies in response to emerging attack patterns.
2. Faster Detection and Remediation Cycles
Modern DAST tools plug directly into the places where developers already work, from version control to ticketing systems. Vulnerabilities are flagged in real time and pushed into the same workflow as any other bug. The practical impact is shorter detection and fix cycles, which lowers the chance that a slight oversight grows into a full-blown incident. For security leaders, this translates into something measurable: less dwell time for attackers and a stronger case for ROI.
3. Lower Cost Compared to Manual Testing
Penetration tests are still indispensable, especially for business logic flaws. But manual pen testing is expensive, infrequent, and hard to scale, unless you use Agentic AI-powered solutions like Terra. DAST fills some of that gap by running continuous, automated scans for common runtime weaknesses, leaving security teams and external testers free to focus on the problems automation can’t solve. The result is often broader coverage (albeit with less depth) at a lower cost.
4. Compliance-Ready Reporting
Regulations and frameworks like PCI DSS, GDPR, and OWASP ASVS often demand proof that applications are being tested against known risks. Many DAST platforms can generate structured reports that meet some of these requirements. While no tool alone guarantees compliance, these reports reduce the back-and-forth with auditors and could give engineers concrete, actionable insights.
Key Features to Look for in DAST Tools
- Accuracy and False Positive Reduction. Strong DAST tools validate findings, correlate results with business context, and reduce noise. The most advanced platforms extend this further with adversarial exposure validation (AEV), testing vulnerabilities under real-world attack conditions to separate theoretical from exploitable risks.
- Ease of Use and Automation. Security cannot become a bottleneck. Tools should integrate seamlessly with developer workflows and enable automated scans triggered by releases, commits, or scheduled intervals.
- Scalability Across Applications. Enterprises may run hundreds of customer-facing applications. Effective DAST platforms handle this scale without requiring linear increases in manual resources.
- Supports modern authentication mechanisms. Most automated tools fail to pass modern authentication mechanisms like MFA, SSO, etc. Make sure your selected DAST tool can help your authentication mechanism run in a fully authenticated mode.
- Comprehensive Attack Surface Coverage. Modern enterprises rely on APIs, microservices, and complex workflows such as shopping carts, authentication steps, and role escalations. A valuable DAST platform must support robust API testing across these deep pathways.
Top 10 DAST Tools for 2025
1. Terra Security
Terra is not a scanner but an agentic-AI-powered, continuous penetration testing solution. Instead of relying on static crawlers, it uses a swarm of specialized AI agents that work as skilled human penetration testers, probing, adapting, and reasoning through application flows. They can scale as needed and continuously learn and adjust to business logic in real time.
All findings are prioritized by business impact and delivered in compliance-ready formats. Plus, its human-in-the-loop component ensures human experts validate edge cases and complex results. This balance provides the best of both worlds: the speed and breadth of automation with the judgment and precision of seasoned security professionals.
Best for: Enterprises seeking more than DAST capabilities, including autonomous, scalable, and business-aware pen testing.
“With agile releases, even small updates can introduce new threats. Terra's continuous Agentic change-based pentesting is transformative, ensuring every new or updated feature gets promptly evaluated for exploitable vulnerabilities.”
2. Rapid7 InsightAppSec
Rapid7’s InsightAppSec delivers broad DAST capabilities with deep integration into the Insight cloud platform. It automates web app and API testing, providing interactive dashboards and attack replay functionality to validate findings. Its CI/CD integrations allow scans to be triggered directly in developer pipelines, making it a practical choice for agile teams. Customers highlight its usability and breadth of coverage.
Best for: Web application vulnerability scanning at enterprise scale.
“I like InsightAppSec, which performs a real call without scanning the code. It tests with negative requests as if attackers attack the application. Provides a detailed dashboard to prioritize actions and remediate risks. You can get actionable and accurate insights using this library.”
3. Burp Suite Professional
Burp Suit Pro is, first and foremost, a manual testing framework, but it also includes an active scanner that automates many standard runtime checks, such as cross-site scripting or SQL injection. Its intercepting proxy lets testers inspect and manipulate traffic in real time, while additional tools cover tasks like fuzzing, session handling, and crawl-and-audit workflows. Extensibility through the BApp Store makes it highly customizable, with hundreds of plugins available.
Best for: hybrid testing environments that blend manual and automated workflows.
“It's a powerful and widely used tool for security testing against websites with many features. For beginners, a free version is great to start learning before diving into the full version.”
4. OWASP ZAP
Now branded as ZAP by Checkmarx, Zap is a widely used DAST tool. It offers automated vulnerability scanning, a powerful intercepting proxy for traffic inspection and manipulation, and an extensive add-on marketplace for extending functionality. The open-source tool also supports API testing, some authentication workflows, and scripting for advanced use cases.. While it lacks some enterprise polish of commercial platforms, it offers extensive flexibility and community support with zero licensing costs.
Best for: Open-source adoption and customizable scanning.
“OWASP is quite mature in identifying vulnerabilities. Whether you run the scan manually or as an integrated part of your CI/CD pipeline, OWASP scanners are quite effective.”
5. AppCheck
AppCheck offers deep crawling of complex, client-side applications and APIs, including support for modern JavaScript frameworks. Its vulnerability coverage extends beyond OWASP Top 10, including misconfigurations, cloud security issues, and emerging attack vectors. AppCheck also integrates remediation guidance directly into its reports, helping teams prioritize exploitable flaws over low-impact noise. Executive dashboards present risk at a business level, while technical output provides engineers with actionable detail.
Best for: Organizations seeking clear remediation workflows with minimal friction.
“We tested multiple products head-to-head and compared them with concrete metrics. Appcheck came out above all others tested on almost all parameters, including ability to crawl the site, vulnerabilities found, and extensibility and configurability of the crawl & testing flow.”
6. StackHawk
StackHawk is a developer-first DAST tool. It supports scanning REST, GraphQL, and SOAP APIs in addition to web applications, making it ideal for microservices. Each scan generates reproducible attack payloads and pushes results into developer tools like Jira and GitHub, ensuring vulnerabilities are actionable rather than abstract. While it doesn’t explicitly offer complete API gateway security, its API discovery and testing features help reduce the risk of exposed or misconfigured API endpoints that a gateway might expose.
Best for: Developer-centric vulnerability remediation.
“The StackHawk program has excellent documentation and is easy for a development professional to set up. With StackHawk, we can discover vulnerabilities in a running environment rather than a static environment, which means we are aware of risks to our application in real-time.”
7. Acunetix
Acunetix’s AI-powered deep crawler maps and scans complex single-page applications, APIs, and network assets. Its AI-based JavaScript engine dynamically executes content to uncover client-side issues, while AI-enabled vulnerability verification automatically filters false positives and highlights exploitable weaknesses. The platform’s AI-assisted integrations with CI/CD pipelines and issue trackers streamline remediation, and its AI-supported scalability and compliance-ready reporting make it one of the most advanced automated runtime testing solutions in the market.
Best for: Comprehensive scanning across modern, complex applications.
“Good thing for a web application pentesting; it can give you insight into present vulnerabilities. I recommend using it with an infrastructure scanner (like Nessus) to create a complete testing solution. Also, continuous scanning and a scheduler could be used for a regular security assessment of your web applications.”
8. GitLab DAST
As part of GitLab’s DevSecOps platform, GitLab DAST integrates seamlessly into existing developer pipelines. It complements GitLab’s SAST and IAST offerings, providing a unified AppSec toolset. While it is less feature-rich than a standalone scanner, centralization and developer adoption are its strengths.
Best for: Teams already invested in GitLab seeking seamless SAST/IAST/DAST integration.
“Scan from start code quality, secret detection, license scan, vulnerability scan, package scan, container scan, API security, DAST inclusion is really useful. Some elements still require improvement in the DAST feature set and integration with other security tools using CI/CD pipelines.”
9. Checkmarx
Checkmarx’s DAST module supports automated scanning of web applications and APIs, with built-in crawling to map complex application flows and authentication handling for sessions and APIs. Findings are correlated with SAST and SCA results, so teams can see whether an issue originates in source code, a third-party library, or runtime behaviour. It allows risk prioritization and ranking vulnerabilities based on exploitability and business impact rather than raw counts. Developers can receive results directly in their workflow through Jira, Azure DevOps, and GitHub integrations.
Best for: Enterprises adopting a multi-method AppSec strategy.
“It is so user-friendly, and it is easy to become familiar with all the numerous features. Although I wasn't around for the implementation, I've found that it is relatively straightforward to integrate further functionality. The Scanning tools are all excellent and provide us with all the status and visibility we require.”
10. Bright Security
Bright Security (formerly NeuraLegion) supports modern API-driven environments with REST, SOAP, and GraphQL scanning. It includes API discovery via specification files or schema introspection, and can import HAR files. It offers CLI / API / CI/CD pipeline triggers for scans, with developer-focused reports that aim to reduce false positives. While it's well-suited for many microservices architectures, especially where front‐end APIs and external-facing endpoints are concerned, some edge cases may require additional configuration.
Best for: Developer-first API security testing.
Customer review:
“Bright Security offers an intuitive and user-friendly interface, making it easy to navigate and manage security tasks efficiently. Also, Bright has good security checks for scanning web applications, which is the most important in the DAST.”
Beyond DAST: Rethinking Runtime Security
DAST tools remain a critical layer of application defense, but their limitations are apparent: false positives, shallow coverage, and a lack of business logic awareness. Attackers innovate faster than scanners; compliance-driven reporting alone does not stop breaches.
Terra combines agentic-AI multi-agent testing with human-in-the-loop validation and real-time adaptability to deliver autonomous penetration testing at scale. The platform moves beyond static, point-in-time reports by continuously simulating realistic exploits, ranking vulnerabilities by business impact, and producing compliance-ready documentation. For CISOs and CIOs under pressure to prove ROI, this platform provides a future-ready alternative to legacy scanners and expensive manual pen tests. Book a demo here.
Continue reading
Be the first to experience the future of security.
Secure your spot by leaving your email










