Back
Top CTEM Vendors

Cybersecurity has entered the era of continuous everything: code is deployed continuously, adversaries probe continuously, and volatility is constant. Yet most security programs still rely on point-in-time pen testing, generating an illusion of control in an environment that no longer stands still.
By 2026, organizations implementing Continuous Threat Exposure Management (CTEM) are expected to cut breaches by nearly two-thirds. Resilience now depends on an unbroken discovery, validation, and remediation cycle, and a new generation of AI-powered vendors is emerging to operationalize CTEM and drive this shift.
However, CTEM platforms still vary widely, and each is built for different approaches, scales, security models, and internal capabilities. Understanding these distinctions is essential to finding a solution that fits your environment, team, and operational reality.
What are CTEM Vendors?
Continuous Threat Exposure Management, or CTEM, is a systematic process that enables organizations to continually discover, verify, and prioritize exploitable threats. Contrary to schedule-based scans, the CTEM framework delivers real-time, repeat visibility into an organization's exposures, so that security teams can focus on the most applicable risks.
CTEM vendors deliver solutions that execute this constant process, including:
- Continuous pen test
- Pen test as a Service (PTaaS)
- Adversarial Exposure Validation (AEV)
- Attack surface management (ASM)
- Breach and attack simulation (BAS)
- Continuous automated red teaming (CART)
- Vulnerability management (VM)
- Threat intelligence
- Auto-validation tools
Mature CTEM programs also often integrate directly with ticketing and workflow systems, allowing validated threats to be assigned and resolved without delay.
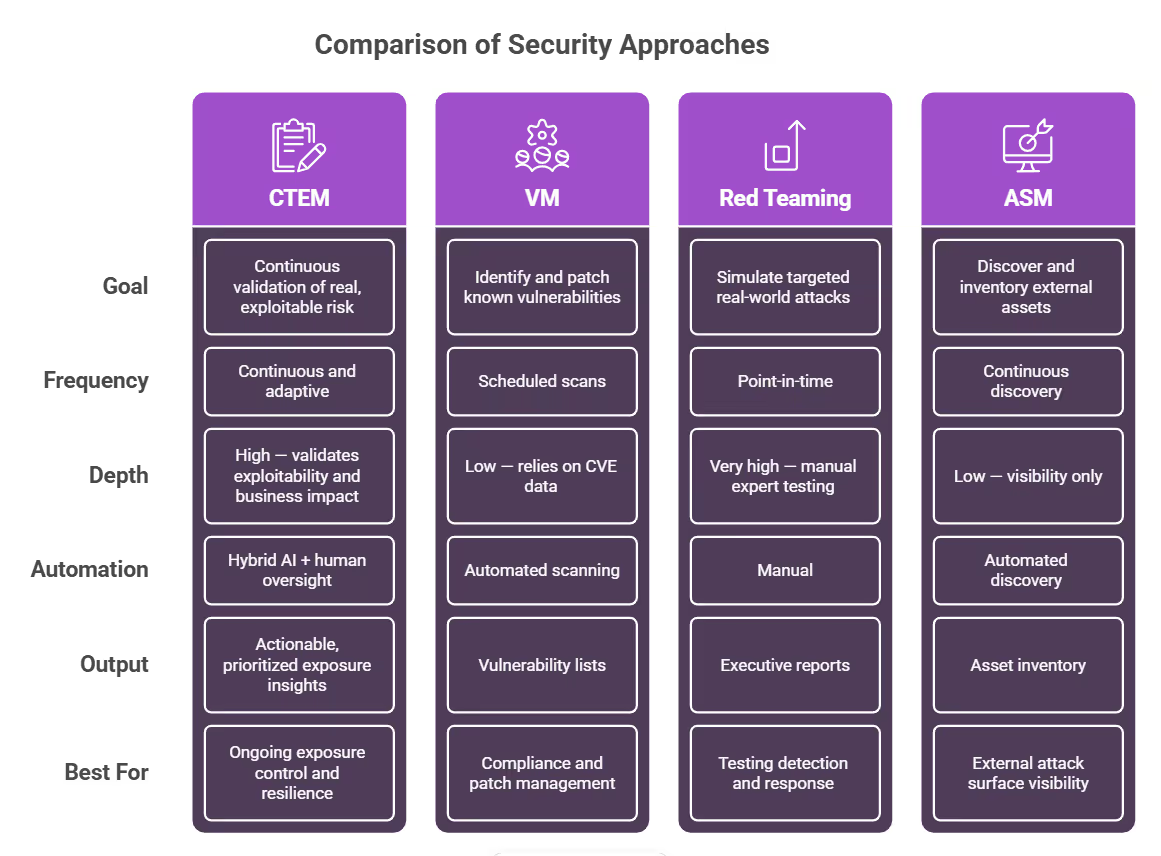
CTEM vs VM, Red Teaming, and ASM
Unlike traditional vulnerability management, which revolves around detecting and patching known CVEs, CTEM focuses on continuous validation, identifying which exposures are present and exploitable attack paths in the real world. While red teaming delivers valuable but periodic insights, CTEM operationalizes that mindset into a sustained, iterative cycle of discovery, validation, and response.
CTEM also evolves beyond standard Attack Surface Management. Instead of listing exposed assets, it applies exploit likelihood and business impact scoring to translate raw visibility into prioritized, actionable intelligence. To achieve this, CTEM programs typically follow a five-phase cycle defined by Gartner: Scoping, Discovery, Prioritization, Validation, and Mobilization.
Benefits of CTEM Vendors
1. Confidence in Actual Exploitability
Most security teams already have visibility but lack certainty. CTEM vendors extend beyond the theoretical by using automated simulation and contextual knowledge to confirm exploitable vulnerabilities. With this, security leaders can finally answer the question boards keep asking: “What’s actually at risk right now and what would be the impact?”.
2. Smarter Risk Decisions
CTEM combines business environment logic, such as asset importance and data confidentiality, with risk assessment. Prioritization at a strategic level matches remediation actions to target exposures with the worst impact on operations or finance but with lower technical severity.
3. Continuous, Unbroken Visibility
Where vulnerability management programs operate in defined cycles, CTEM runs continuously, allowing real-time observation of external and internal attack surfaces. By constantly monitoring for new exposures and misconfigurations, they eliminate blind spots and keep the risk posture view up to date.
5 Key Features to Look for in CTEM Vendors
1. Continuous and Adaptive Testing Capabilities
Platforms should perform constant, deep testing that continually adapts to changes in the environment (new code, assets, applications, or threats). Look for vendors who refresh exposure data regularly and apply testing logic that simulates evolving, real-world attacker tactics.
2. Real-Time Exposure Validation
Top CTEM vendors must validate exploitability through secure emulation of live attacks or using automated breach-and-attack techniques. High validation accuracy and minimal false positives are key quality parameters that count far more than static scanning.
3. Exploitability-Based Attack Path Simulation and Prioritization
The platform must visually display attack paths and rank threats based on the likelihood of impact on business-critical targets. Evaluate vendors' correlation of asset criticality with attack path mapping to provide accurate risk ranking.
4. Hybrid Human-AI Model for Precision and Depth
The best CTEM vendors blend AI automation (for scale and pattern discovery) with human expertise (for expert validation and calibration of scenarios). This hybrid approach provides the most comprehensive understanding and the most reliable prioritization.
5. Actionable, Executive-Ready Reporting
The platform must capture in-depth exposure data and distill it into executive-level dashboards. Compare vendors based on their ability to transform reports to support multiple stakeholders and translate conversational remediation status back into existing systems.
Top 10 CTEM Vendors
1. Terra Security
Terra Security serves as the validation engine that transforms visibility into action. It not only identifies exposures through active testing but also verifies which ones are truly exploitable. Its Agentic-AI-powered continuous pen testing solution tests web applications with a human-like red team's reasoning, adaptability, and precision, uncovering real, exploitable risks.
Terra’s multi-agent architecture emulates skilled penetration testers, adjusting strategies in real time based on findings and application behavior. A built-in human-in-the-loop framework ensures every result is accurate, contextual, and safe, bridging the speed of automation with expert oversight.
By running tailored attack simulations that reflect each application’s data sensitivity and business logic, the platform delivers true continuous validation of business-critical attack surfaces.
Best for: Continuous, intelligence-driven exposure validation that complements CTEM programs in modern, application-centric enterprises.
“We’ve been really impressed with Terra Security. Their AI-powered penetration testing makes it feel like a real security researcher is continuously reviewing our app. It goes beyond the usual scanners by understanding business logic and catching things we wouldn’t have thought to test for.”
2. XM Cyber
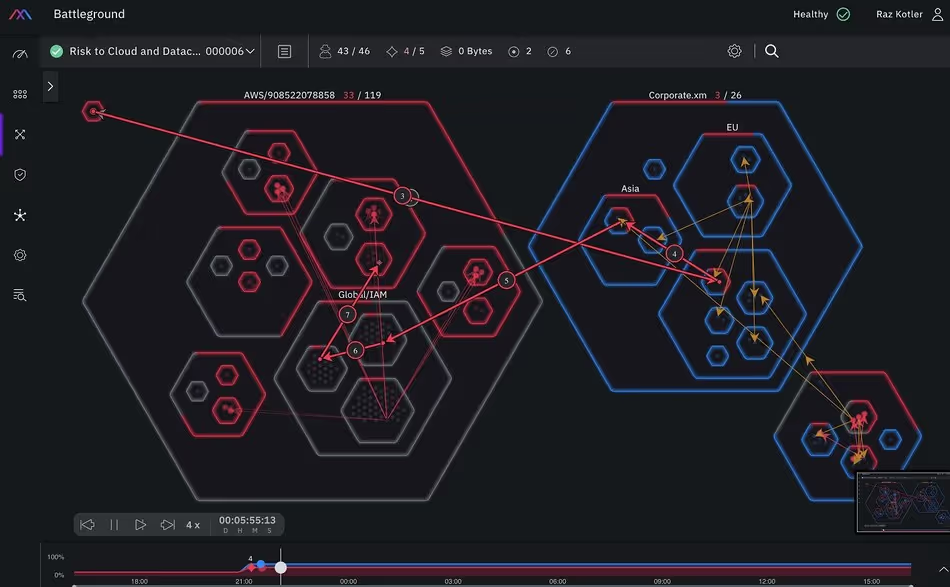
XM Cyber is a hybrid cloud exposure management provider that integrates with AWS, Azure, GCP, and on-premises environments. Its flagship product, Attack Graph Analysis, models the risk from end to end, illustrating how attackers can exploit identity exposures, misconfigurations, and vulnerabilities. Visualizing end-to-end attack paths, the product identifies "Choke Points" where remediation will eliminate the most significant number of attack paths, maximizing effectiveness across the hybrid environment. It also integrates seamlessly into broader data center management workflows, helping teams maintain a unified view of risk across every environment.
Best for: Testing in diverse hybrid environments.
“The continuous monitoring and real-time alerts are what I like best about XM Cyber's security solution. It gives me peace of mind knowing that my network is being constantly monitored and that I will be notified if any potential threats are detected.”
3. Tenable
Tenable bridges traditional vulnerability management and CTEM maturity through its Tenable One Exposure Management platform. It unifies visibility across cloud, identity, and web environments, correlating vulnerabilities with business impact and exploitability. Predictive prioritization and attack path analytics provide security teams with continuous assurance of what truly matters, transitioning from static CVE tracking to live exposure insights.
Best for: Scaling from vulnerability management to CTEM-grade continuous exposure visibility.
“My overall experience with the platform has been very positive, especially in terms of performance and capabilities. I was closely involved in both implementing and operating Tenable in our organization. The installation was easy and quick to configure.”
4. Picus Security
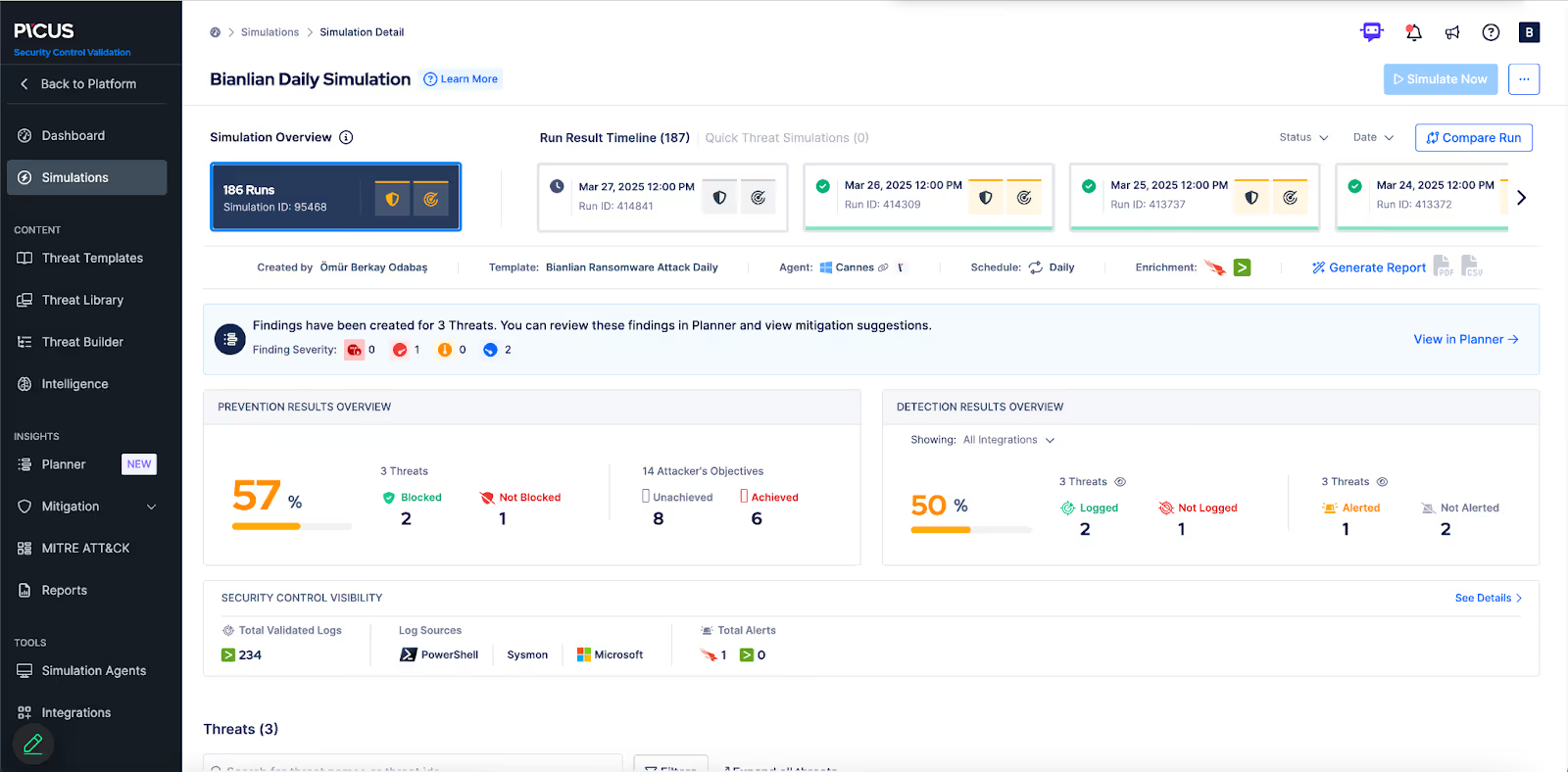
Picus Security is especially effective at prioritizing exposure based on exploitable risks within a customer's ecosystem. Its platform utilizes BAS and automated penetration testing, along with a proprietary Exposure Score, to regularly test controls against real-world attack techniques. This adversarial exposure validation eliminates a significant theoretical vulnerability backlog, prompting security teams to address high-impact exposures that utilize real attack paths.
Best for: Exposure Prioritization through its proprietary Exposure Score.
Customer Review: “The platform makes it possible to validate whether our defenses are effective continuously”.
5. Cymulate
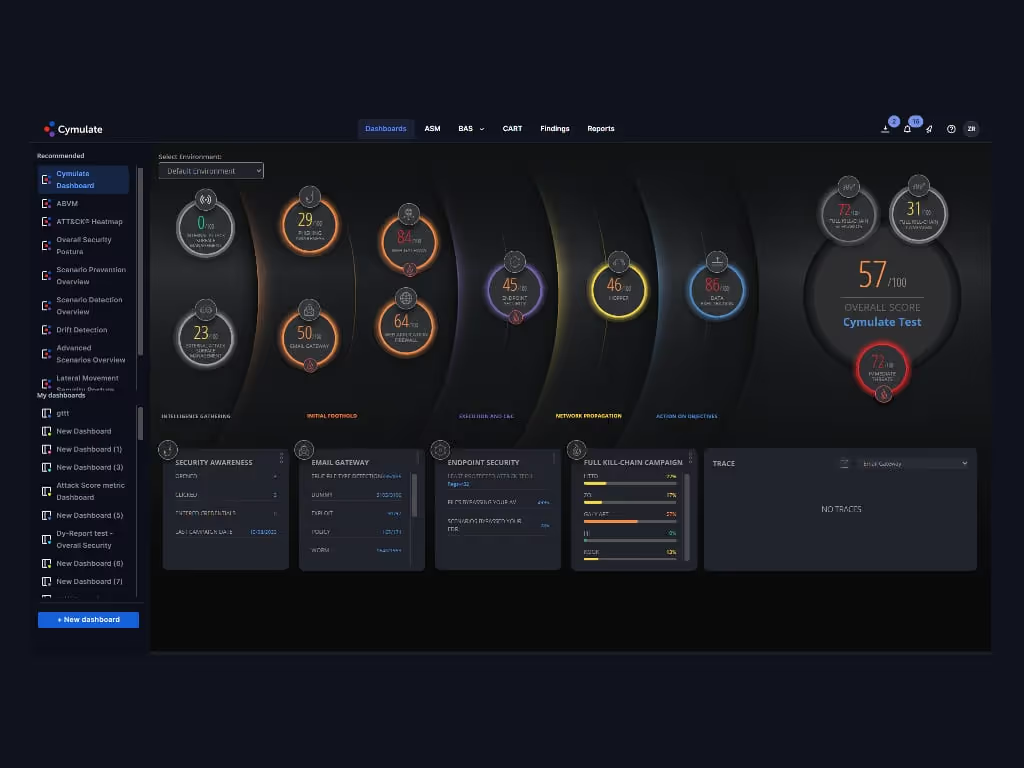
Cymulate is most relevant to Continuous Validation, with its Exposure Management Platform founded in BAS and CART. It continuously tests production-safe, in-the-wild attack scenarios against an organization's security controls (EDR, SIEM, firewalls) in cloud, on-prem, and hybrid environments. This adversarial exposure validation testing provides empirical proof of exploitability, where controls fail, and where to focus remediation to achieve quantifiable gains in threat resiliency.
Best for: Continuous Validation through its Exposure Management Platform.
“Cymulate turns continuous, safe attack simulations into actionable, MITRE-mapped fixes with one-click retesting. It centralizes App/Email/Web/EDR/WAF/ASM validation, integrates with our stack, and gives exec-ready reporting to prove risk reduction month over month.”
6. Ionix
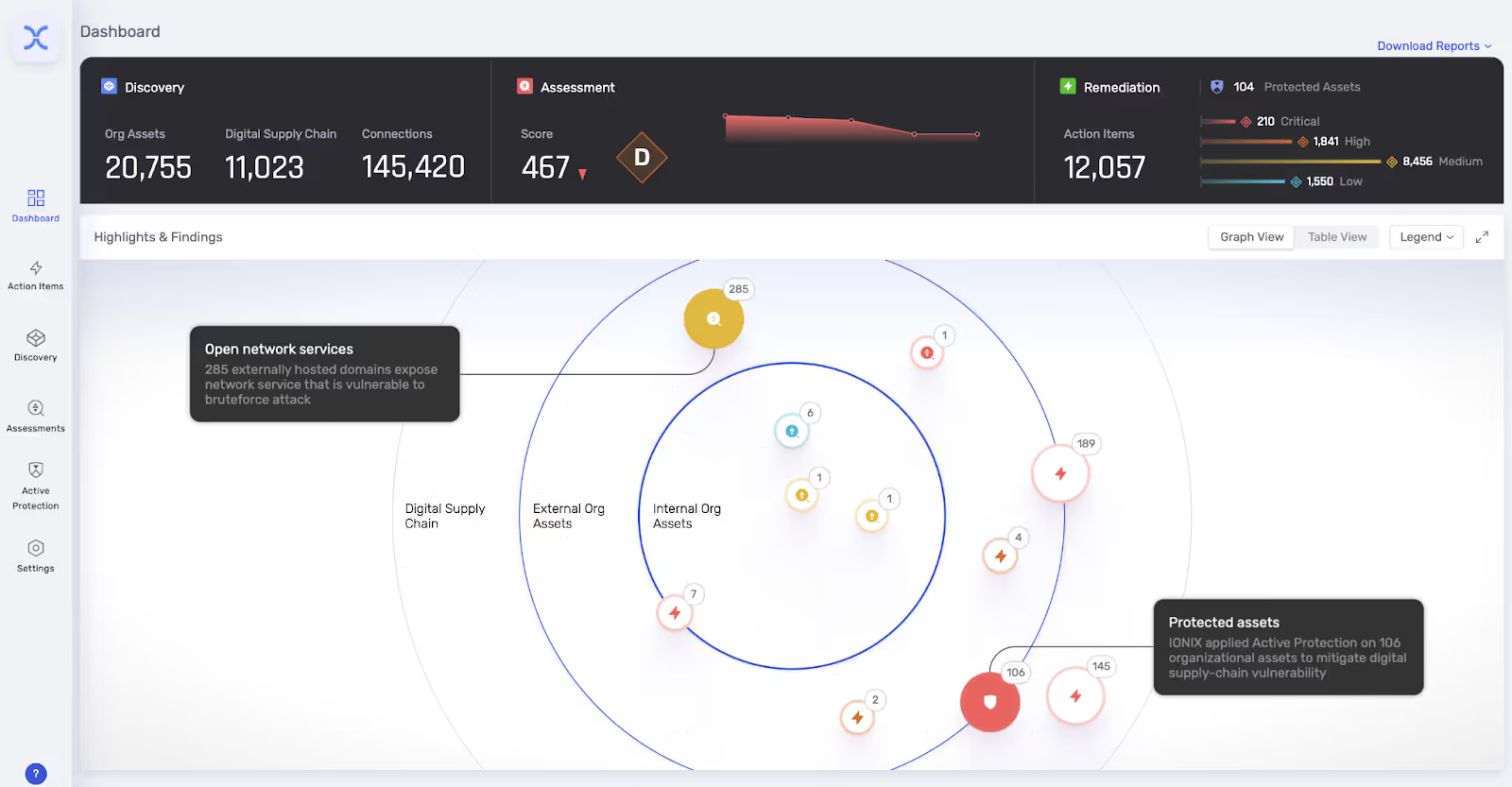
Ionix began as an EASM product but evolved into a comprehensive CTEM offering. It continuously discovers, analyzes, and manages the entire external attack surface, including vendor-managed assets and the digital supply chain. Its "Connective Intelligence" offers visibility into all internet-facing assets using multi-layered prioritization that checks exploitability to create consolidated, actionable remediation workflows.
Best for: Attack surface discovery, including vendor-managed assets and software supply chain risk.
“IONIX enables us to manage all our assets from one platform. We can view all assets, login pages, web services, and more from a single location. It automatically scans everything, allowing us to discover new information about our organization. We don't need to add each asset or interface manually.”
7. RiskRecon
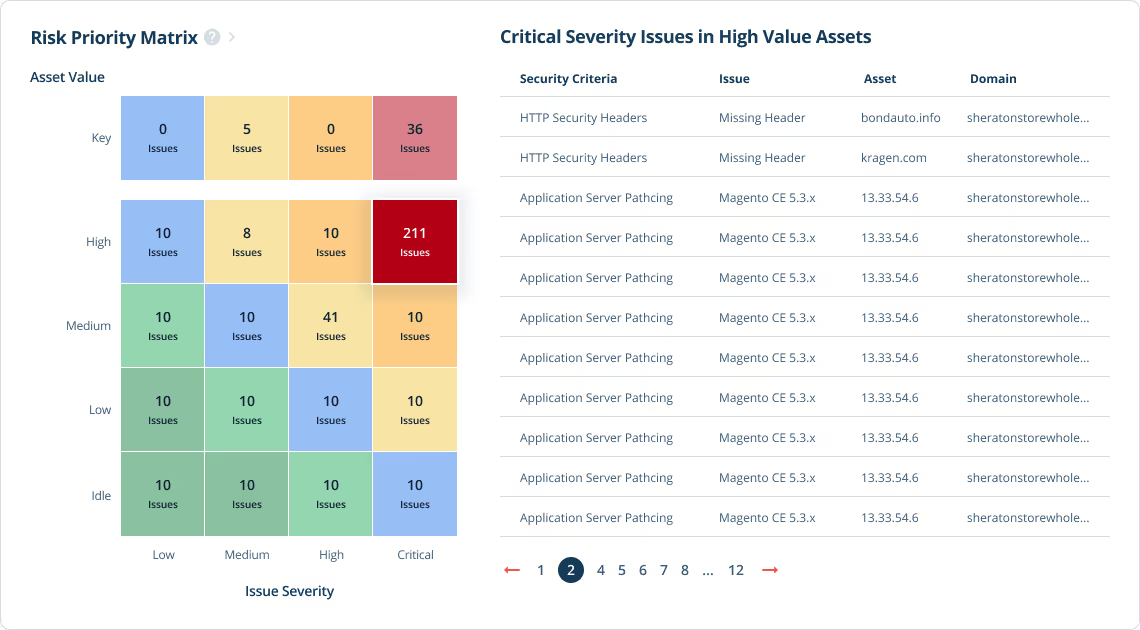
RiskRecon provides CTEM primarily through automated, data-driven exploit scores and risk ratings for an entire company's extended digital environment, including its third-party vendors and software supply chain. It continuously scans for external risk exposures, performs in-depth cyber risk analysis of vendor behavior, and generates a customized Risk Priority Matrix to enable security teams to focus resources on the risks that pose the highest potential financial and business impact.
Best for: third-party and software supply chain risk management.
“It's a detailed report that covers all aspects of IT security. Start with application-related vulnerability, certificate-related issues, end-of-license software, any malware signature identified, and any data leak about the organization.”
8. Veriti
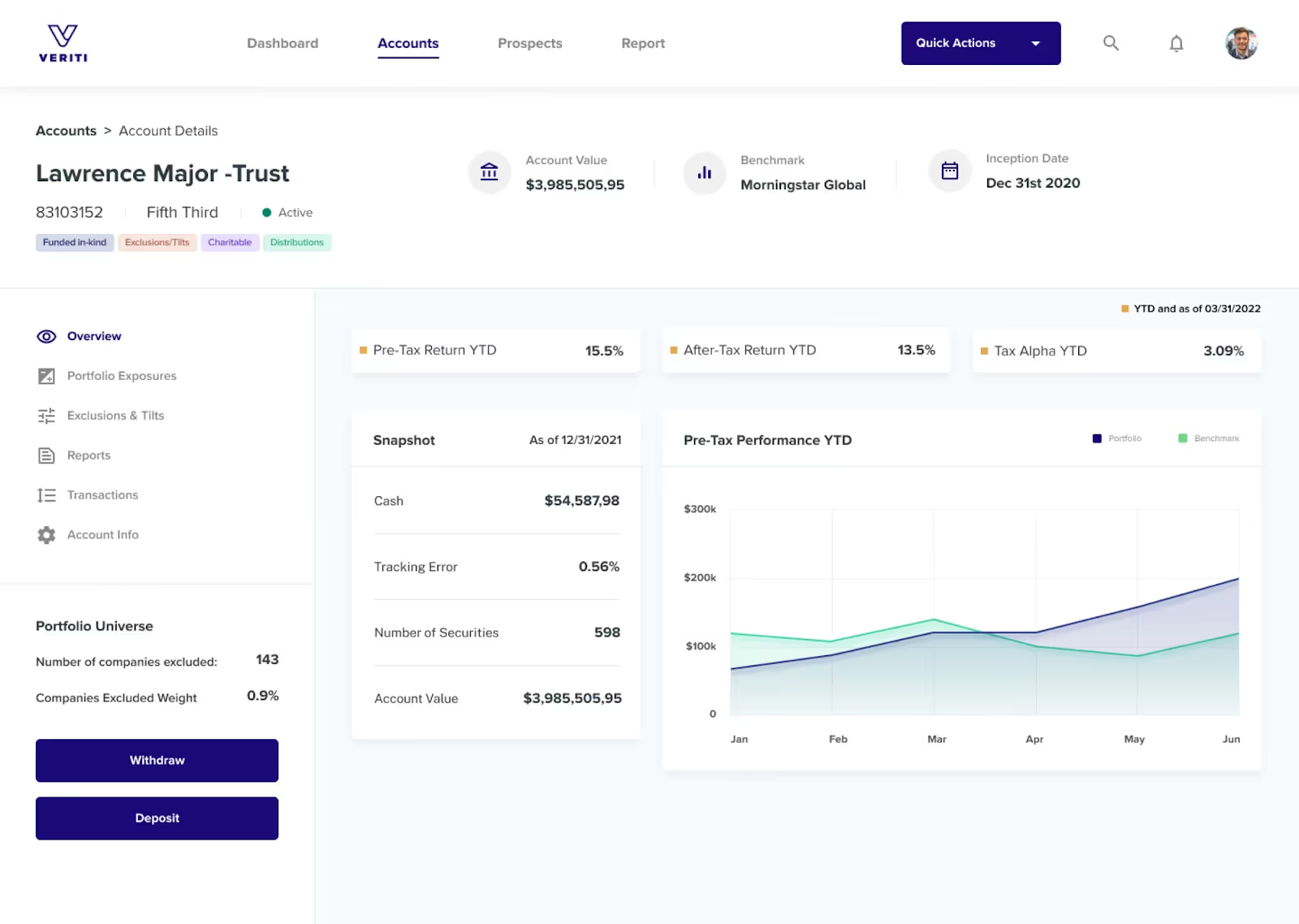
Veriti is an Exposure Management solution with a significant focus on automated analysis of control and optimization across multi-vendor deployments. It continually ingests and compares data from over 70 security products (including cloud, EDR, and firewalls) to identify misconfigurations and gaps. It prioritizes the resultant exposures by business context and exploitability and orchestrates non-disruptive remediation actions, such as policy hardening, securely and directly through the integrated tools.
Best for: maximizing the coordination of a diverse, multi-vendor security stack.
“It is easy to integrate, and once integrated, the insight you get about your organization is priceless. In addition, their overall knowledge about safeguards allows them to help you be better at what you do, as they are willing to go the extra mile to share their knowledge with you.”
9. Rapid7
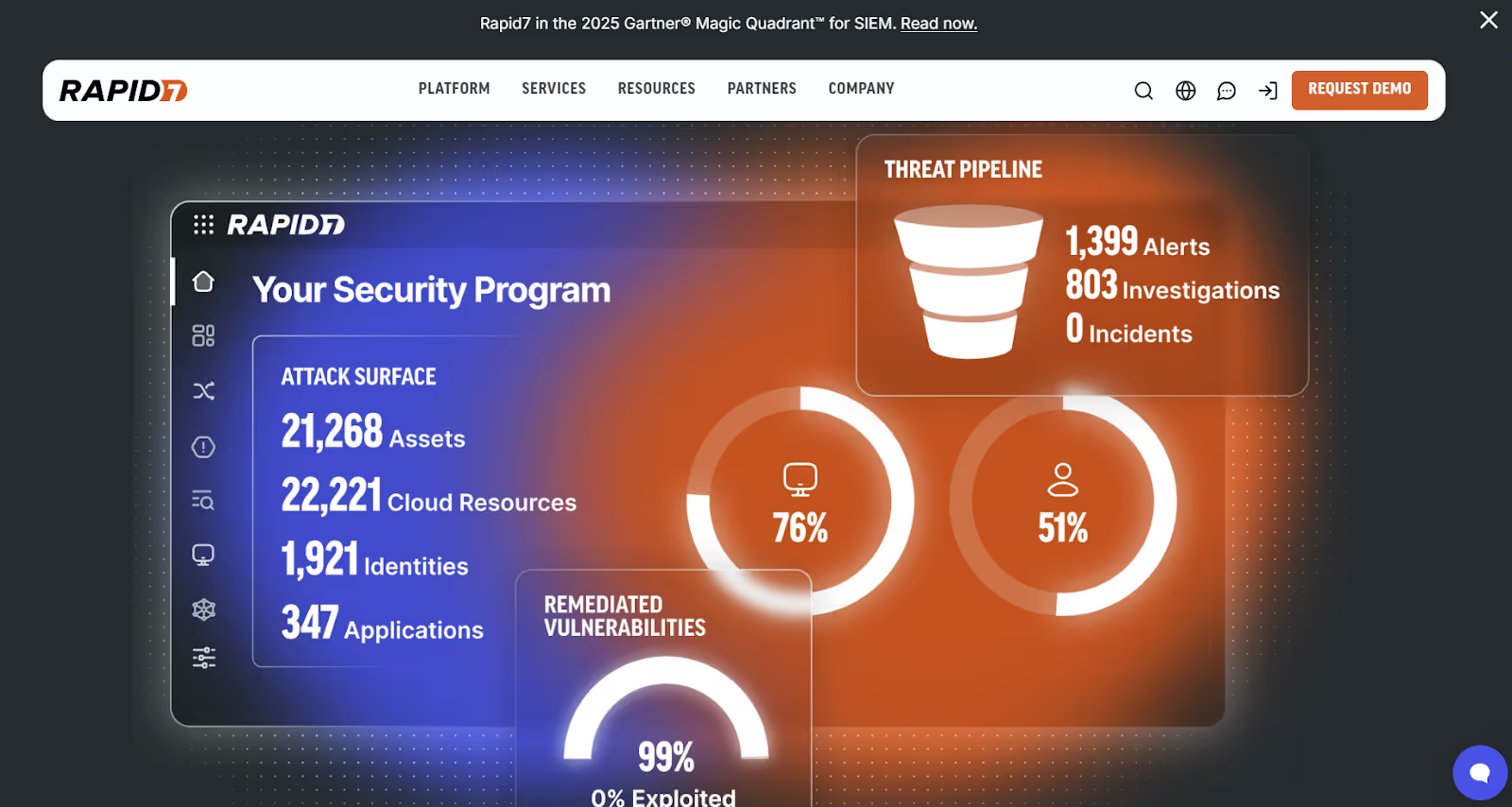
Rapid7’s Insight platform connects vulnerability, cloud, and threat intelligence data into a CTEM-aligned workflow. InsightVM provides live vulnerability analytics, while InsightCloudSec extends visibility into misconfigurations and cloud exposures. Combined with real-time exploit intelligence from Threat Command, it supports complete CTEM cycles, from discovery to mobilization, within a single interface.
Best for: Organizations seeking an integrated CTEM ecosystem across hybrid and cloud environments.
“I personally think R7 goes above and beyond with their product offering in that they provide a host of other information to help you remediate the vulnerabilities, and they display the information in a very digestible way. This tool is scanning all of our devices, and even helping us find what devices we are not accounting for.”
10. Cyberproof
Cyberproof offers a CTEM solution as part of a managed security services package, leveraging its Interpres-based platform to provide an agentless, threat-led defense management solution. Their platform actively correlates the organization's tailored threat profile with the performance of existing security controls (EDR, SIEM) through a patented agentless integration. It identifies principal security control vulnerabilities, prioritizes based on real-world exploitability, and provides practical recommendations for optimizing the existing security environment.
Best for: using CTEM as a managed security service as part of an existing system.
From Vulnerability Noise to Actionable Signal
Modern security teams are drowning in vulnerability data, and CTEM is a game-changer in turning noise into clarity. The strongest CTEM vendors go beyond discovery, helping security teams understand which exposures put the organization at risk and how to fix them quickly.
Built for web application security, Terra Security’s agentic-AI platform serves as the validation engine behind continuous exposure management, combining the adaptability of human reasoning with the precision of autonomous AI.
Its multi-agent system performs deep, context-aware penetration testing that mirrors real-world attacker behavior. It continuously validates exposures as environments evolve, while a human-in-the-loop ensures real-time operational intelligence. This results in fewer false alarms, clearer prioritization, and an always-up-to-date view of actual business risk. Book a demo and start operationalizing CTEM today.
Be the first to experience the future of security.
Secure your spot by leaving your email











