Back
Top 10 Adversarial Exposure Validation (AEV) Tools
%20Tools.avif)
You probably already know where your vulnerabilities are, at least on paper. The backlog of theoretical CVEs, risk alerts, and scan results says so. But which of those are truly exploitable? Which ones map to an attacker’s real-world path into your environment?
The unknown is the most dangerous part of your security posture, and adversaries know it. In 2024, vulnerability exploitation accounted for 14% of breach entry points, nearly triple from the year before. Meanwhile, 56% of old vulnerabilities remain actively exploited, showing that known issues linger without action.
Instead of assuming everything marked “critical” is truly exploitable, Adversarial Exposure Validation (AEV) tools simulate real attacks to validate which exposures matter most across your attack surface, not just your controls.
Top Adversarial Exposure Validation Tools at a Glance
Best overall: Terra Security
Easiest to get started: NodeZero by Horizon3.ai
Best compliance reporting: Picus Security
Best for large-scale testing: AttackIQ
Best for continuous integration: BreachLock
What Are Adversarial Exposure Validation Tools?
Adversarial Exposure Validation (AEV) is the process of identifying which vulnerabilities in your environment are exploitable by testing them the way a real attacker would. It moves beyond traditional vulnerability scanning and static breach simulation by introducing dynamic, adversary-driven testing logic that mimics actual attack chains.
Adversarial Exposure Validation tools operationalize this strategy. These automated decision support systems for offensive security identify exploitable exposures, trace realistic lateral movement paths, and clarify how chained weaknesses might impact businesses.
This capability is especially critical in complex web applications, where business logic flaws often go undetected by traditional scanners. AEV tools help organizations reduce alert fatigue, prioritize real risk, and align remediation with actual attacker behavior, all while supporting continuous delivery models.
AEV is now a core component of Continuous Threat Exposure Management (CTEM), providing CISOs and security leaders with validated, contextualized insights that drive smarter remediation strategies at scale.
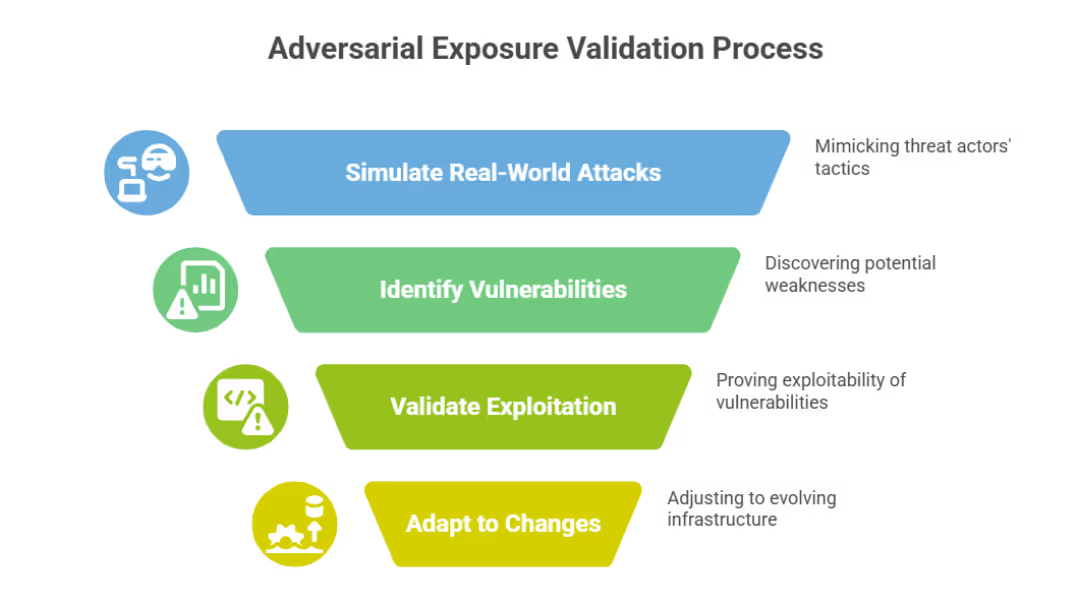
Why Use Adversarial Exposure Validation Tools?
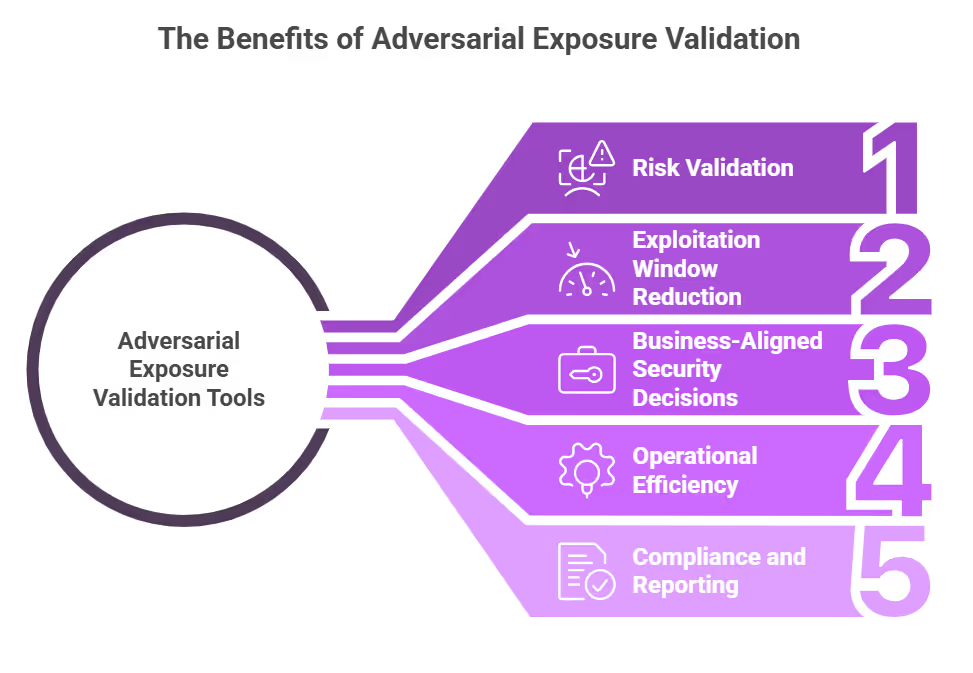
- Turn Unknowns Into Validated Risk: AEV platforms verify which exposures attackers are more likely to exploit, helping AppSec and DevSecOps teams cut through noise and prioritize confidently.
- Close the Exploitation Window: AEV tools give real-time insights that adapt as your code, infrastructure, or users change, significantly reducing the time vulnerabilities are exposed.
- Improve Business-Aligned Security Decisions: Validation makes it easier to tie vulnerabilities to real business risks, such as compromised customer flows or exposed PII. It empowers security leaders to make decisions that align with compliance and revenue protection.
- Operational Efficiency at Scale: External penetration testing doesn’t typically scale across hundreds of apps. AEV tools automate this process with accuracy, removing the bottlenecks of costly human-led testing and inconsistent outputs.
- Support for Compliance and Reporting: Leading platforms integrate with regulatory frameworks, helping companies continuously meet requirements like SOC 2, HIPAA, or PCI-DSS; and prove it, with validated findings.
Key Features to Look for in AEV Tools
1. Real-World Adversary Simulation
Effective AEV tools must do more than replay attack scenarios. They emulate the strategic behavior of actual adversaries, adapting in real-time based on system responses, architectural layout, and environmental cues. This real-world simulation enables platforms to uncover nuanced vulnerabilities, including chained exploits and complex escalation paths.
2. Full Attack Surface Coverage
Leading tools extend their reach across authenticated environments, internal systems, APIs, and third-party integrations. Unlike traditional tools that scan from outside, robust AEV platforms enable white-box testing to uncover deeply embedded exposures often missed by network-centric BAS or vulnerability scanners.
3. Human-in-the-Loop Validation
While automation drives scale, human oversight remains essential for accuracy. Best-in-class platforms employ a hybrid model where AI performs broad, continuous attack emulation. At the same time, experienced security professionals validate critical findings, fine-tune scenarios, and ensure ethical boundaries are never crossed.
4. Business Logic Awareness
A distinguishing mark of advanced AEV solutions is their ability to model and exploit logic unique to each application or environment, such as user privilege flows, financial transaction abuse, or workflow manipulation. This capability is especially crucial for customer-facing web applications where business logic flaws are the most impactful and challenging to detect. When mapped to risk management models, these insights help organizations assess which logical exposures represent material business risk.
Top 10 Adversarial Exposure Validation (AEV) Tools
1. Terra Security
Terra Security is the first agentic-AI platform for offensive cybersecurity focused on web application pen testing, with a human-in-the-loop mechanism. Unlike web app scanners, DAST tools, or manual pen testing vendors, Terra uses a swarm of fine-tuned AI agents that behave like skilled human testers. They dynamically adjust attack plans based on application logic, workflows, and real-time findings. It’s one of the few solutions that can simulate complex, business logic-aware attacks across 100% of your attack surface.
Terra supports a continuous, change-based penetration testing validation, white-box support, and a built-in human-in-the-loop mechanism to ensure accuracy and safety. The platform’s reports are compliance-ready and laser-focused on actionable, business-relevant insights.
Best for: Enterprises seeking deep, real-time validation of web app vulnerabilities with business logic complexity.
“With agile releases, even small updates can introduce new threats. Terra's continuous Agentic change-based pentesting is transformative, ensuring every new or updated feature gets promptly evaluated for exploitable vulnerabilities.”
2. AttackIQ
AttackIQ is a mature breach and attack simulation (BAS) platform built to rigorously assess the effectiveness of security controls across modern enterprise environments. It supports detailed adversary emulation across endpoint, network, identity, and cloud layers, using a content library mapped to the MITRE ATT&CK framework. With internal support for emulation scripting, security engineers can replicate specific threat actor behaviors and observe how their environment responds at each step.
Best for: Large-scale security teams needing broad coverage and MITRE ATT&CK mapping.
“Overall experience with the product is great! The product has provided so much insight into our systems and improved our overall security posture. Product can be in the high end in terms of pricing, but it is money well spent!”
3. Picus Security
Picus Security simulates how attacks unfold across each phase of the cyber kill chain. The platform includes a continuously updated attack library drawn from the latest threat intelligence to replicate advanced threat actors' tactics. It also allows analysts to measure control gaps using coverage reports aligned with standards such as NIST CSF, ISO 27001, and MITRE ATT&CK. It is especially valuable for uncovering how lateral movement or privilege escalation might succeed within segmented environments.
Best for: Teams needing compliance-ready validation across multiple control layers.
“As the offensive security team, our job is to find the answer to whether we are ready against evolving and new adversarial campaigns. We conduct various red team exercises, and the insights provided by Picus help us design the most relevant scenarios.”
4. Pentera

Pentera runs agentless, safe attack simulations in production, chaining multiple exploit techniques to replicate real adversary campaigns. It covers internal, external, cloud, and Git repositories, with modules for credential exposure, lateral movement, and privilege escalation. Distributed architecture supports large-scale testing, while AI-driven prioritisation ranks exploitable findings and integrates with tools like ServiceNow and Jira.
Best for: Enterprises needing scalable, chained-attack simulations across hybrid environments without agents or downtime.
“The ability of the tools to lessen the time of penetration testing versus the manual way. The validation is a unique feature that most tools don't have. With these tools, you can easily manage, implement, and deploy the software in just a few hours.”
5. BreachLock
BreachLock delivers a SaaS-based pen testing platform that integrates AI automation with manual testing, especially across cloud, application, and network environments. It offers DevOps-native features, including API integration, container security, adherence to API security checklists, and regular incremental testing. The platform’s continuous testing capability, supported by a global team of ethical hackers, makes it uniquely suited for dynamic development teams.
Best for: Engineering-led organizations needing plug-and-play AEV integration.
“I was thoroughly impressed with their professionalism and expertise. From the initial consultation to the final report, the team was communicative, thorough, and provided valuable insights into the security of our web application.”
6. Cymulate
Cymulate enables security teams to assess specific vectors (such as phishing entry points, endpoint resilience, internal pivoting, and web application exposures) through independently deployable test modules. Its Immediate Threat Intelligence module enables simulation of the latest real-world attacks within hours of discovery. While it lacks business logic awareness, Cymulate effectively validates the efficacy of layered security tools and educates stakeholders on organizational posture.
Best for: Mid-sized teams needing multi-vector exposure validation.
“The dashboard customization and reporting system could be improved, as the overall score is calculated as an average of all assessments conducted since day one, potentially limiting more granular insights.”
7. NodeZero by Horizon3.ai
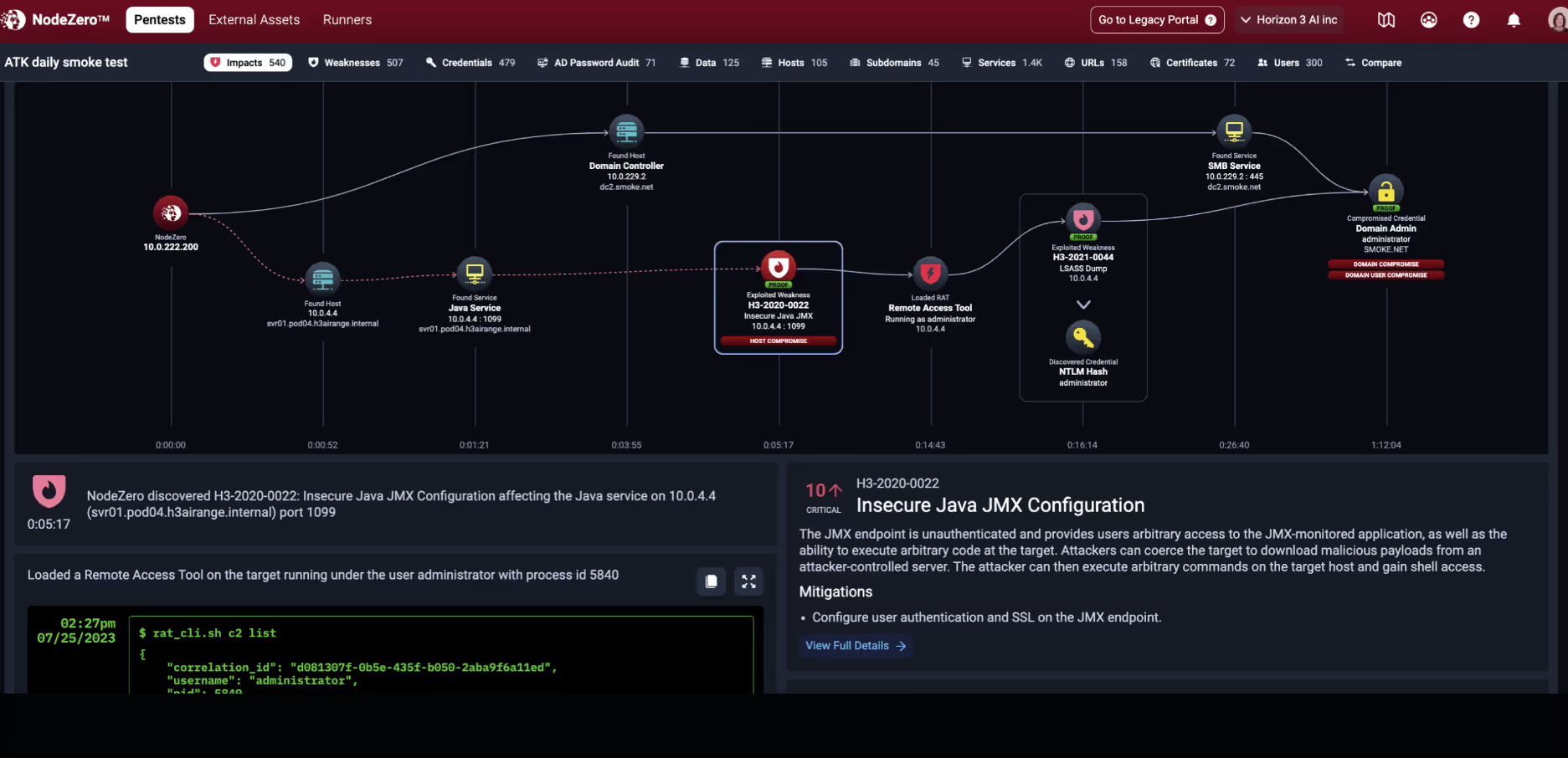
NodeZero offers fully autonomous red teaming without the operational overhead typical of traditional pen testing tools. It requires no persistent agents or prior access credentials, yet it can identify exploitable paths by chaining together misconfigurations, exposed secrets, and privilege escalation opportunities. It mimics post-exploitation techniques and provides clear narratives of each attack chain, including initial foothold, lateral movement, and potential impact.
Best for: Teams seeking fast setup and autonomous red teaming.
“Our experience with NodeZero so far has been great. It is like having a pentest with quantifiable results and the ability to fix and retest every week. We could do the setup during our trial period and have it ready when we decide to purchase.”
8. SafeBreach
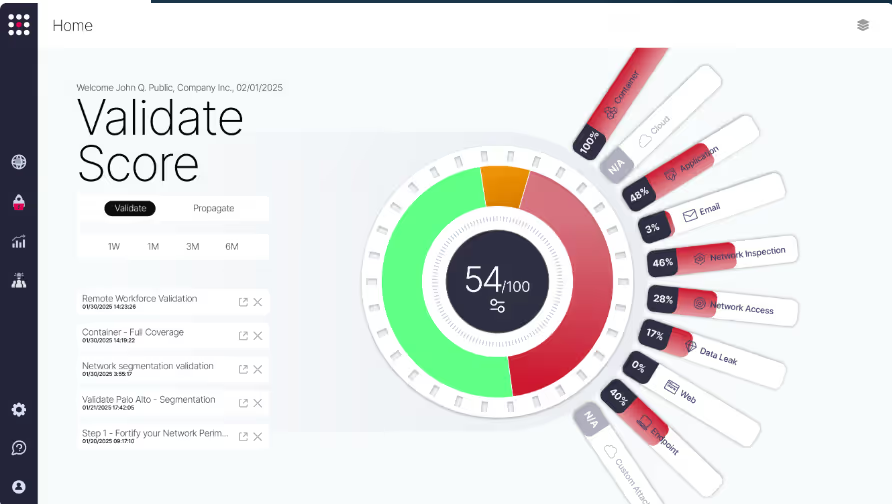
SafeBreach offers an extensive library of attack methods, drawn from real-world threat actor TTPs and malware campaigns. Security teams can use this playbook to stress-test EDRs, firewalls, and other controls across multiple attack vectors in production-like conditions. The platform integrates SIEM, SOAR, and endpoint solutions to automate response playbooks and accelerate remediation. It excels in environments where continuous validation of defenses is prioritized over exploit chaining or custom logic testing.
Best for: Teams focused on control coverage and repeatable simulation.
“Working with Safebreach has been exceptional. From a customer perspective, our account management team could not be more on point; they are fantastic. The executives of the company are truly accessible as well, and are genuinely excited about the product.”
9. XM Cyber
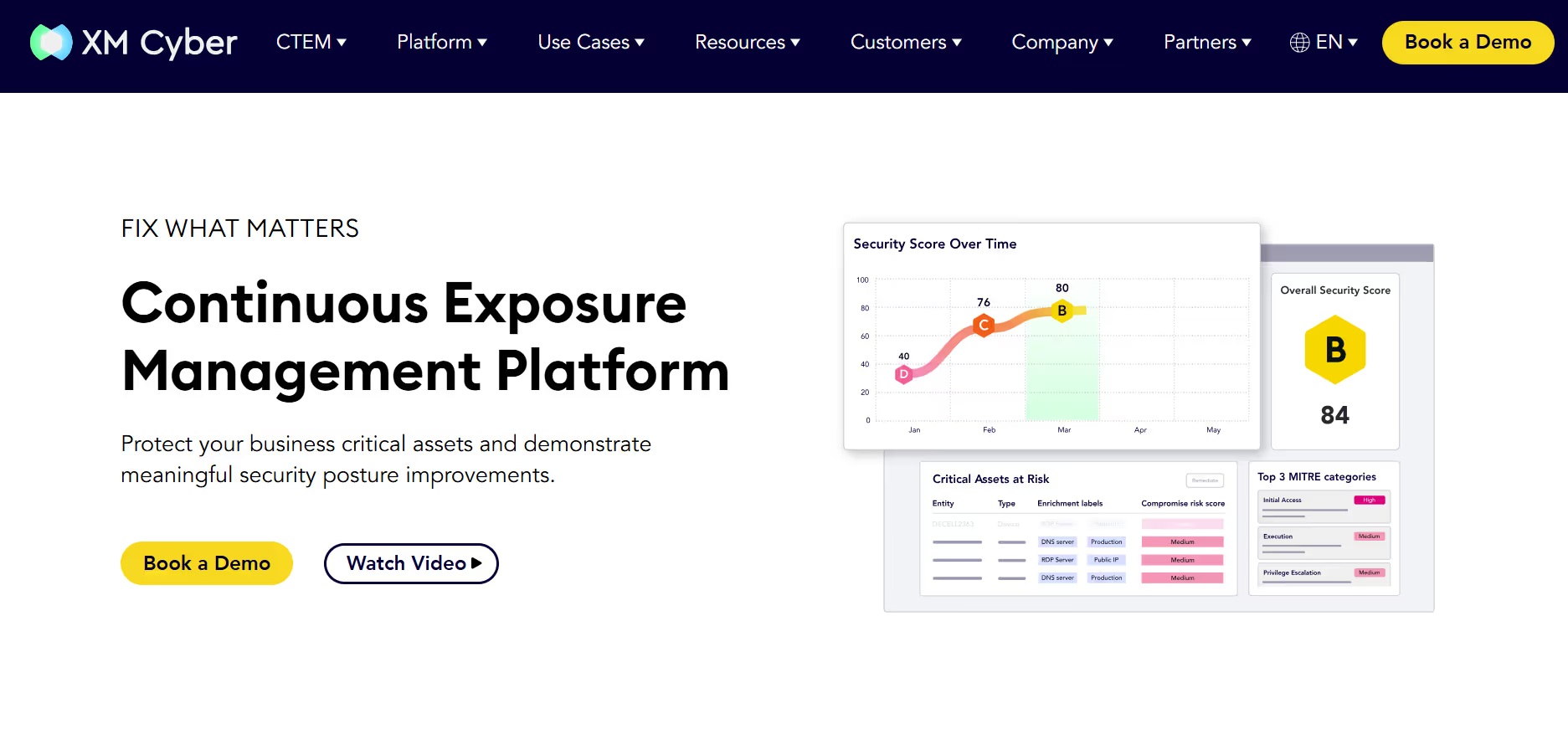
XM Cyber enables continuous exposure management by combining attack path mapping with security control validation. It identifies how threat actors could move from low-value assets to crown jewels by chaining small misconfigurations and overlooked weaknesses. Integrations with CMDB and vulnerability scanners allow security teams to close exposures proactively.
Best for: Hybrid infrastructure teams needing attack path visualization.
“Very friendly and competent staff. Implementation was straightforward. During and after the implementation phase, the direct contact person handles any outstanding or upcoming questions or problems.”
10. Scythe

With Scythe, teams can script full campaigns with staged payloads, encoded commands, and callback infrastructure, reflecting threat actor TTPs from frameworks like MITRE ATT&CK. Security teams can test detection gaps and incident response readiness using real-time SIEM and EDR integrations telemetry. Scythe is best suited for advanced operators who want to build and iterate on live threat actor models in realistic network conditions without operational risk to production systems.
Best for: Ideal for teams with red team experience and threat intelligence maturity.
“The thing I like best about SCYTHE is their support team. The platform is easy to set up and is scalable based on your level of knowledge.”
Validate First, React Later
In today’s high-speed software environments, vulnerability validation is table stakes. The shift from theoretical to validated risk is the only way to keep pace with adversaries who exploit real-world attack paths, not abstract CVEs. AEV tools are the natural evolution of offensive security, bridging detection with real insight and action.
Terra Security delivers this next-gen capability at scale. With multi-agent reasoning, deep business logic awareness, and full CI/CD integration, Terra helps organizations test what matters continuously and accurately. For CISOs and security leaders navigating compliance demands, shrinking teams, and rapid releases, Terra makes offensive security scalable and strategic.
Ready to validate what really matters? Learn more here.
Be the first to experience the future of security.
Secure your spot by leaving your email








